What’s New
The Flashpoint Ignite Technical Indicators app for Splunk provides users with the ability to index and analyze Flashpoint’s Indicators of Compromise (IoC) data via the Technical Indicators API. The app is easily configured and allows for custom indexing intervals and data windows to retrieve relevant IoCs. The app seamlessly integrates with existing Splunk data, allowing for efficient IoC querying and identification to generate actionable insights.
Why it Matters
The Flashpoint Splunk app is optimized for targeted investigation and threat hunting. It provides significant value to Splunk users by allowing them to proactively identify and mitigate potential threats based on Flashpoint’s actionable intelligence, reducing their organization’s risk exposure and improving their overall security posture.
How it Works
Admin users with a valid Flashpoint Ignite API token can navigate to the Splunk website to install and set up the app.
Input your API token, then select one of the indexes on your Splunk instance where you want Flashpoint IoC data to be indexed. The app will index this data with a source type of Flashpoint IoCs so you can easily distinguish it from other data stored there.
Choose the frequency at which you would like the application to index new IoCs, and specify the age of IoCs to index based on their last seen at date.
Once the setup is complete, the app will immediately start indexing Flashpoint IoC based on your selections. This data is accessible via a lookup table called Flashpoint IoC lookup, enabling users to leverage this data manually through search and reporting. It can also be accessed via our New Hunt page.
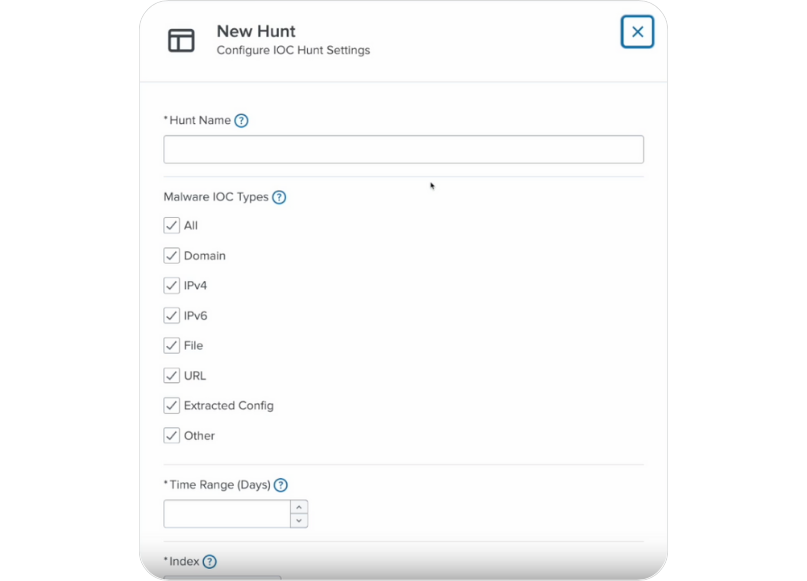
On the Hunts page, select New Hunt. This will specify information about what you want to hunt for within Flashpoint’s IoC data, and against your organization’s data.
For example, you can search Flashpoint IoCs for any potentially compromised file hashes against an index that you store company file download logs in.
Select the source types you want to look in and the fields you want to include. If a match is found, you can use this information to mitigate or prevent further compromise.
Previously run investigations are stored on the Hunts page. Easily rerun these investigations by clicking on them rather than creating a new hunt each time.
Learn More about Flashpoint Integrations
Get the most out of your security investments by integrating Flashpoint into your workflow where it matters most. Learn more here.

