The Cybersecurity and Infrastructure Security Agency (CISA) has added more vulnerabilities to Binding Operational Directive (BOD) 22-01. Also known as the Known Exploited Vulnerabilities (KEV) Catalog, BOD 22-01 provides organizations with a curated list of vulnerabilities that have been—or are actively being—exploited in the wild.
While only Federal Civilian Executive Branch Agencies (FCEB) must adhere to CISA BOD 22-01 remediation and reporting requirements, many organizations in the private sector are including the KEV Catalog in their workloads. Since the initial publication, the list has been repeatedly updated. New vulnerabilities have been added and we expect this to be a continuing trend. However, even though the CISA KEV can be a valuable resource for vulnerability management teams, it should not be an organization’s primary driver for prioritization—as it is solely dependent on CVE.

Exploited Vulnerabilities Can Take Months to Make KEV List
Dark Reading speaks with Brian Martin, Vulnerability Historian at Flashpoint to discuss the limitations of the CISA KEV and how organizations can stay ahead of potential threats.
BOD 22-01’s three directives for vulnerability management
For those unfamiliar with BOD 22-01, it is a significant directive that has garnered media attention. It is impacting many organizations; especially those that support US government agencies. To summarize, there are three specific points involving vulnerability management that organizations should know:
- Beholden organizations must establish and detail an ongoing remediation process for the vulnerabilities that CISA identifies. If asked by CISA, federal enterprises must provide a copy of their process.
- Each vulnerability listed in the Known Exploited Vulnerabilities Catalog must be remediated within its specified timeline, which may vary.
- Organizations complying with CISA BOD 22-01 will be required to report on the status of vulnerabilities listed in the repository.
Over 9,500 high to critical vulnerabilities last year
The Known Exploited Vulnerabilities Catalog is a major shift from the traditional views of vulnerability management (VM). Most VM frameworks place emphasis on CVSS scores. However, severity scores provide no context into whether an issue has actually been exploited or used in the wild.
While the KEV catalog addresses this shortcoming it does not lessen the existing workload for security teams. Rather, it increases it. CISA BOD 22-01 is meant to supplement federal enterprise and the private sector’s vulnerability management efforts. It does not replace Binding Operational Directive 19-02, which still requires federal enterprises to remediate high and critical vulnerabilities within 30 and 15 days respectively. In 2022, there were over 9,500 vulnerabilities with a CVSSv2 score of 7.0 to 10.0. Using CVSSv3 and the same scoring, that number increases to over 15,800. Therefore, FCEB agencies will need a detailed and flexible VM process to remediate those issues and the KEV Catalog.
What should be prioritized—exploitability or high severity?
There can be conflicts in regards to prioritization and remediation if CISA BOD 19-02 and 22-01 are compared side-by-side. If federal enterprises were expected to remediate over 9,500 vulnerabilities as they appeared, should they focus on the KEV Catalog?
BOD-22-01’s strict vulnerability remediation timeline
Even if organizations intend to remediate these issues, they may not have enough time to comply with CISA. Depending on the vulnerability remediation tools and data at their disposal, adhering to BOD 22-01’s timelines may be near impossible. When the KEV Catalog was first announced, 100 of its initial 292 entries were due in two weeks:
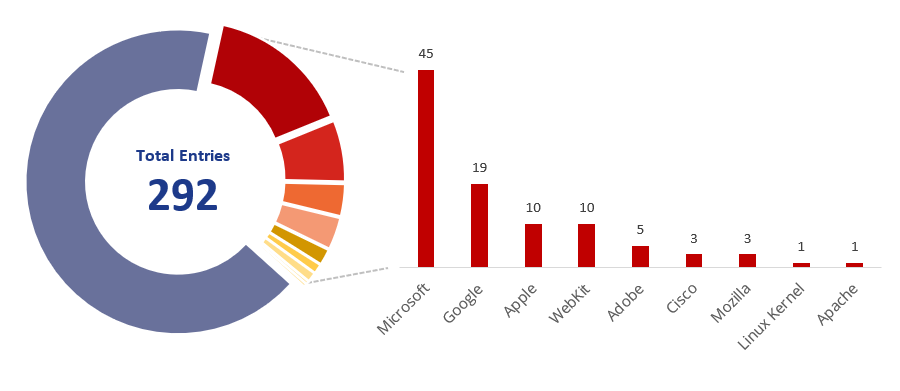
Those 100 vulnerabilities were disclosed by the following vendors—each with a remediation deadline of November 17 (two weeks):
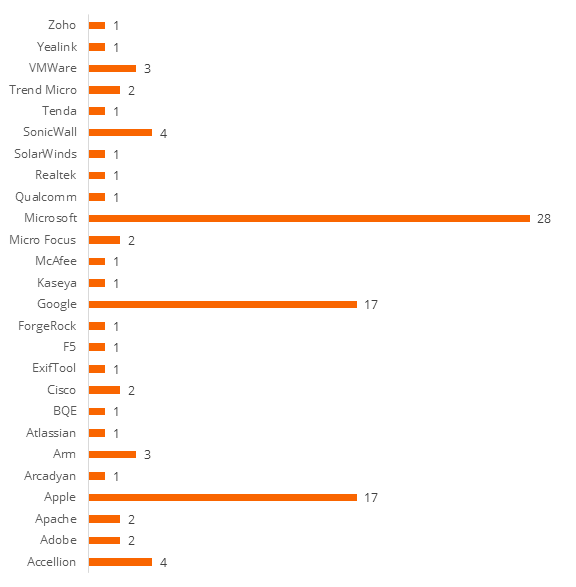
Having only 14 days to resolve an issue is extremely difficult, since multiple steps need to take place before an issue can be fixed or mitigated. And over the following months, many more vulnerabilities have been published sporadically with the same remediation requirement. However, before remediation can take place, organizations will need to research what is needed to patch. Then they need to test the patch on development systems. But before that, security teams will have to know if their systems even contain those vulnerabilities. For most enterprises, the go-to method for that is scanning. However, reliance on this tool is one of the main reasons that enterprises often fail to meet CISA’s requirements.
Limitations of vulnerability scanning
When used alone, vulnerability scanners can be a detriment to your Vulnerability Management Program. This is because nothing can be done until the scanning vendor provides a signature. This process can take days or weeks.
Unfortunately, organizations will likely experience this delay often. A considerable number of KEV Catalog vulnerabilities have NVD assigned CVSSv2 scores that fall below 5.99. As of September 2023, 20 percent of all KEV vulnerabilities have a CVSSv2 score that is less than 5.99. This is significant for three reasons.
- Issues scored beneath 5.0 are viewed as “moderate” or even “low” risk
- Even a CVSSv2 5.0 issue can be serious (see: Heartbleed)
- Scanning vendors do not fully map to CVE
Delays in creating vulnerability scanning signatures
Most providers do not provide complete coverage, opting instead to create signatures for high to critical severity scores. Then they focus on issues that receive considerable attention. This means that it is highly likely that many lower-scored KEV Catalog entries did not have signatures at the time of its release.
In the case of zero-day or n-day vulnerabilities, this delay will last even longer. It isn’t a secret that many scanning vendors base their signatures on CVE/NVD data. So for issues like CVE-2022-22620, the Apple Webkit zero-day, CVE will designate them as RESERVED status, signifying that MITRE is in the process of aggregating information, or waiting on a researcher or vendor to provide them details. However, until that data is compiled the entry will contain no details. This means that NVD is also likely to be empty, since it is dependent on CVE. Once it is published, another delay can occur during the time it takes for NVD to analyze and then assign a CVSS score.
The Apple Webkit zero-day was added to the KEV Catalog on February 11 and had a due date of February 25. FCEB agencies will have already been required to remediate it, but CVE has had it classified as RESERVED for over two weeks preventing scanning vendors from deriving a signature for it.
Several other issues shared the same fate. Added back in October, the entries CVE-2021-38003 and CVE-2021-38000 had also been in RESERVED status for a lengthy period of time. The good news is that their CVE and NVD entries are now populated. The bad news is that both issues were published by NIST on November 23, 2021, after CISA’s due date of November 11, 2021. Worse yet is that for over a month, CVE-2021-38000 had underwent reanalysis, meaning that its entry had been out-of-date during its mandated remediation period:
In these situations, how long will triaging, researching, and remediation be delayed? If it is taking over two weeks for CVE/NVD to populate their data, how long will it then take scanning vendors to create corresponding signatures? On top of that, simply running the scan can be expensive and time consuming, so perhaps it will be pushed to the next monthly, or quarterly network scan. This doesn’t even account for the research that will then be required, since base CVE/NVD entries are often unactionable.
Prioritizing CISA KEV Catalog vulnerabilities
In order to remediate in a timely fashion, organizations will need comprehensive and actionable vulnerability intelligence. Flashpoint’s VulnDB® fully maps to the BOD’s entire vulnerability catalog and contains all of the latest vulnerability details.
The following can also help organizations prioritize CISA BOD 22-01 issues:
Create an asset inventory
Triaging BOD 22-01 vulnerabilities could kick-start the process of building an asset inventory. Using this as an opportunity to ensure that your inventory list is updated accurately will enable more efficient vulnerability management in the future.
Using an asset inventory along with comprehensive vulnerability intelligence allows a team to swiftly identify which systems are vulnerable without relying on weekly or even monthly scans. With an asset list in your mind, you can determine if new vulnerabilities disclosed in the CISA BOD 22-01 affect any deployed software.
This quickly rules out any vulnerabilities that don’t apply to your environment, and may cut the list down to make it more manageable. While the vulnerabilities within BOD 22-01 may be the most exploited, it doesn’t guarantee that affected software is commonly deployed. For example, does your organization use the following?
- BillQuick Web Suite
- Serv-U Secure FTP / Serv-U Managed File Transfer Server
- FreeType
- Tenda AC15 Router
- Duplicator Plugin for WordPress
- DrayTek Vigor
If not, you no longer have to remediate over a dozen vulnerabilities. Eliminating irrelevant entries will lessen your current workload, and as the catalog grows, doing so will save valuable resources in the future.
Check the software bill of materials (SBOM)
For software like FreeType, although security teams may be familiar with what it is, they may not know if it is integrated into any deployed software. This highlights the benefit of development teams maintaining a Software Bill of Materials, so they can more easily determine if vulnerable third-party libraries might impact them. That leads to the question of whether your vulnerability intelligence feed has comprehensive third-party library coverage or not. Unfortunately, CVE / NVD does not.
CISA’s ongoing reporting requirements
Organizations strictly relying on publicly sourced data or scanning technologies are at a disadvantage. BOD 22-01 is designed to put both federal agencies and the private sector on the path to proactively address risk. But if the data and tools at their disposal are unable to allow them to remediate or mitigate those issues in a timely manner, the needle won’t move forward.
Regardless of their resources or tools used, FCEB agencies are still required to report on the status of unpatched KEV Catalog vulnerabilities. And if Log4Shell is any indication of how long remediation processes actually take, then chances are many agencies are begrudgingly reporting numerous unpatched vulnerabilities, or are reporting many slowdowns in the remediation process. Timely vulnerability management not only improves the image of the organization, but it also allows BOD 22-01 to fulfill its purpose of strengthening the United States digital infrastructure against cyberattacks.
Visibility into discovered-in-the-wild vulnerabilities
In addition, it would be helpful to know which of these vulnerabilities are being exploited in-the-wild were originally discovered in-the-wild. Such zero-day attacks often represent high-end exploits that are used by serious threat actors, nation states, and/or sold for tens or hundreds of thousands of dollars. Identifying these types of vulnerabilities could serve as a short list of issues to patch immediately.
At BOD 22-01’s release, 125 entries were discovered-in-the-wild, which is over one third of the list. While alarming, compare that total to other vulnerability tracking services and databases, many of which do not even track that point of data. As of September 2023, over 250 vulnerabilities have been discovered in the wild since the KEV’s launch in 2021.
In the State of Vulnerability Intelligence: 2022 Midyear Edition report, we detailed the various services and projects that track these types of zero-day vulnerabilities, while also comparing it to VulnDB®. Having a timely view into all these vulnerabilities, is a significant benefit to a security team working to triage an otherwise overwhelming number of issues.
Detect, prioritize, and remediate risks faster
In order to remediate effectively, organizations need comprehensive and actionable vulnerability intelligence. Many of CVE/NVD’s deficiencies result from their inability to proactively seek out newly disclosed and updated vulnerabilities. Organizations now have access to over 330,000 vulnerabilities, and are aware of new issues 21 days faster on average compared to NVD. Get a free trial to see how Flashpoint revamps vulnerability management capabilities.


