What is SEO poisoning?
SEO poisoning is a black-hat technique of abusing and tricking search engine algorithms to affect how they index and rank sites.
Search engines utilize various factors like keywords, backlinks, and more to determine the relevance and order of displayed websites based on user queries.
This technique is exploited by cybercriminals to deceive unsuspecting internet users and lead them to compromised websites, where their systems can be infected with malware.
These threat actors often target specific industries or individuals by utilizing keywords that align with the victims’ daily activities.
The chosen keywords are carefully selected to match the attackers’ lures and frequently correspond to the name of the malware payload. Unlike other phishing attacks that tailor their content to each victim, SEO poisoning campaigns typically employ static lure content.
Common tactics employed in SEO poisoning campaigns involve enticing victims with counterfeit document templates or office software. The payloads are often disguised with fake icons, creating an illusion of a harmless PDF file while executing malware upon opening.
However, in some cases, threat actors do package the payload with a legitimate version of the software the user intended to download.
The following are several major SEO poisoning campaigns that highlight common tactics, techniques, and procedures (TTPs) associated with this type of cyberattack:
Gootloader
Gootloader is an SEO poisoning campaign that leverages an array of SEO-poisoned sites to infect victims. When an unsuspecting internet user visits the website, embedded code forwards the visitor’s IP address, referrer string, unique server ID, and user agent to the attacker’s domain and then determines whether a lure should populate.
If the visitor searched for a specific term and is located within a targeted geographic region, or if they are using a certain operating system, the site creates a visible overlay instead of redirecting the victim.
Gootloader runs an array of over 400 servers that control compromised WordPress sites. Many search queries target medical and healthcare organizations.
Gootloader infections have led to executions of Cobalt Strike, the trojan Kronos, as well as REvil ransomware.
BATLoader
BATLoader is a malware that is often associated with SEO poisoning campaigns, where threat actors lure victims to sites with trojanized productivity or office tools.
After a victim visits a search result, BATLoader’s Traffic Direction System determines whether they should be redirected to a fake message board with a download link.
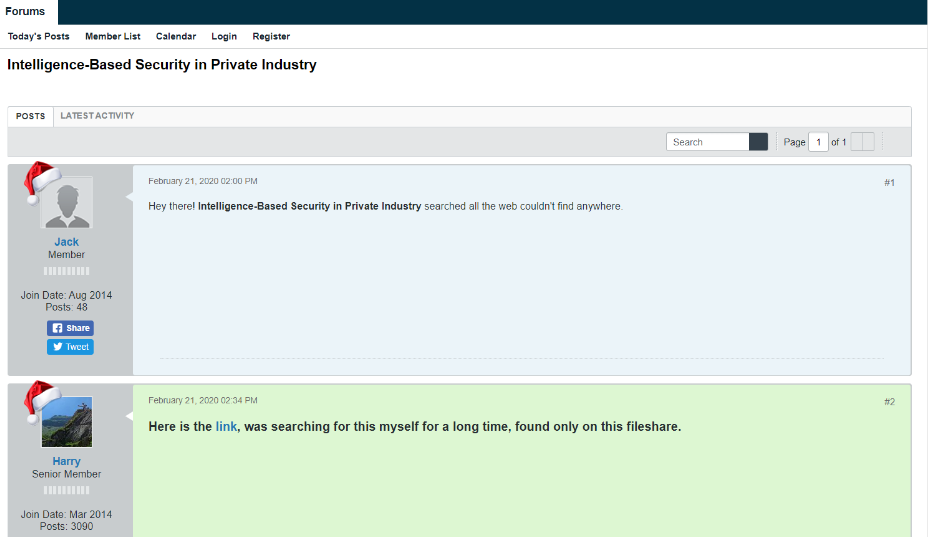
A 2021 leak revealed that BATLoader’s TTPs overlap with those of the new-defunct ransomware gang Conti.
Solarmarker
The Solarmarker SEO poisoning campaign uses a wide array of keywords targeting the remote workforce. Similar to Gootloader, Solarmarker employs an arsenal of compromised WordPress sites.
Each of those sites runs a plugin that generates a directory in which attackers upload a malicious payload. In many cases, the Solarmarker lure prompts users to download a fake PDF document.
The perpetual cycle of cybercrime
SEO poisoning will likely continue to rise in popularity, and while it gives threat actors a reliable initial access vector it does provide long-term challenges.
Even if done correctly, SEO is extremely finicky as rankings change everyday. However, in the case of black-hat SEO, it is even more volatile as most search engines derank sites for abusing the algorithm—therefore creating a perpetual cycle of cyberattacks.
As their own sites become deranked for malicious behavior, threat actors seek to steal new sites that are newly created, or have high authority scores in order to avoid wasting time creating one from scratch.
Unfortunately, threat actors have two main ways to accomplish this.
- Attacking content management systems (CMS)
Threat actors will often target content management systems such as WordPress, with common vulnerabilities to gain control of multiple sites at once. - Exploiting vulnerabilities in themes and plugins
Plugins and themes installed on CMS platforms often have vulnerabilities. Therefore, threat actors may seek to exploit weak login credentials to CMS admin panels to gain access to vulnerable sites.
Once threat actors gain site access, they can modify the site’s content or inject malicious code. Then, threat actors will continue to use it to host future SEO poisoning campaigns until it is shut down or deranked—prompting them to steal more.
How to protect against SEO poisoning
To avoid falling for SEO poisoning schemes, organizations should create and implement application allow lists. In addition, user education should be tailored to the changing threat landscape, and users should be familiarized with common lures employed by malware campaigns.
As SEO poisoning domains change quickly, Flashpoint recommends to block active content within browsers to prevent redirection or lure overlays.
In addition, many of the TTPs employed by malware campaigns using SEO poisoning remain similar to other malware campaigns after the initial infection.
Flashpoint recommends implementing detection schemes surrounding the execution of any JavaScript, VBS, .ISO, .MSI, or .IMG files from within a .ZIP archive.
Flashpoint also recommends removing the default file association of JavaScript and VBS files with Windows script interpreter “wscript.exe” through group policy changes.
To further mitigate risks to CMS platforms, organizations should ensure that all themes and plugins are kept up-to-date with regular security audits and a robust vulnerability management program to ensure that their site is not abused by threat actors.
Protect against digital threats with Flashpoint
Threat vectors are converging at breakneck speeds which makes addressing risk increasingly difficult. Sign up for a free trial to stay ahead of potential targeted threats.


