GLOSSARY
Navigating the Evolving Landscape of Insider Threats: A Strategic Guide
An insider threat refers to the risk posed to an organization’s security by individuals within the organization. These individuals include employees, contractors, or partners. They have access to sensitive information or systems. They may intentionally or unintentionally misuse that access to compromise security.

As digital landscapes evolve, so does the complexity of security threats from within. Insider threats cover a spectrum. This ranges from accidental data breaches to calculated infiltrations. They have become a pivotal area of concern for modern organizations. Recognizing and reducing insider threats demands a sophisticated understanding and approach. It is distinct from traditional external threat defenses.
Understanding Insider Threats
Insider threats vary widely in intent and impact. They range from employees who inadvertently mishandle data to those who maliciously exploit their access for personal gain. Threat actors and Advanced Persistent Threat Groups (APTs) often intensify these threats. They actively recruit insiders to aid in their illegal campaigns. This makes it crucial for organizations to guard against external breaches and to also fortify from within.
Demystifying Insider Threats
Addressing insider threats begins by challenging common misconceptions:
- Myth #1: Not all insider threats are intentional. Many are the result of negligence or lack of awareness.
- Myth #2: An effective Insider Threat Program (ITP) is not just a set of tools. It is a comprehensive strategy. It involves cross-functional collaboration and integrated investigative functions.
- Myth #3: Insider threats cannot be entirely prevented by an ITP alone. Robust foundational security practices are crucial.
The Insider Threat Intelligence Cycle
Effectively managing insider threats requires a structured approach through the Insider Threat Intelligence Cycle, which includes:
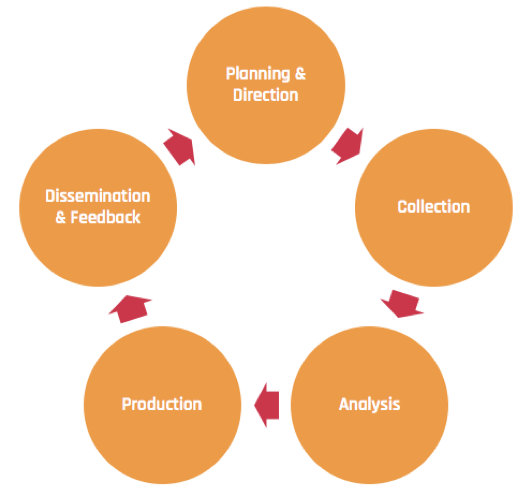
- Planning & Direction
Establishing intelligence requirements and objectives initiates the insider threat program. This is done to address critical knowledge gaps. Examples include identifying communication methods for recruitment and assessing potential insider threats. - Collection
Gathering data from internal and external sources provides crucial insights to fulfill intelligence requirements. These sources include user behavior analytics and deep web forums. - Analysis
Scrutinizing collected data enables the deduction of actionable conclusions. Examples include identifying communication platforms for recruitment and common insider tactics. - Production
Insights from analysis inform the development of policies and controls. Examples include employee monitoring and training programs to mitigate insider threats. - Dissemination & Feedback
Collaborating with stakeholders refines proposed plans. This ensures a comprehensive approach to combat insider threats.
The Unique Risks and Challenges Posed by Insiders
Many security operations centers (SOC) and incident response (IR) teams are primarily configured to combat external threats. These threats distinctly manifest through detectable network breaches. Insiders inherently bypass many of the defenses against external threats. This is due to their legitimate access to company resources. Insider threats can be as damaging as any external attack. They are challenging to detect. They are potentially more devastating due to the access and trust granted to employees. This is true even if the issue is a simple mistake, such as sending sensitive information to the wrong recipient. However, the risks are even more significant for more nefarious activities like data theft for financial gain.
A malicious insider can possibly already have access to critical IT systems. This includes company assets such as intellectual property, and the personal information of customers and employees. This makes them a formidable risk. They deserve the same level of attention as external threats. Disgruntled employees can become insiders. They can steal data. They advertise their access within an illicit marketplace or forum. From there, they can be recruited by immoral competitors, cybercriminals, or even nation-state intelligence services. Therefore, insiders are a risk that must be managed. They require a blend of technology and understanding of behavior to properly analyze a threat before it possibly impacts the organization.
Mitigating Insider Threats
Mitigating insider threats requires a blend of proactive strategies and responsive measures. It involves deploying advanced analytical tools such as User Behavior Analytics (UBA). UBA helps detect unusual behavior patterns and potential threats by correlating data from various sources. Additionally, maintaining strong identity and access management protocols is essential. Continually educating employees about security best practices is also a necessary step toward minimizing risks.
Cyber threat intelligence teams need visibility into information sources. These sources can monitor the deep and dark web, as well as illicit marketplaces and forums in real-time. They must forward any information pertaining to indications of insiders soliciting company data. Security teams should also have a mechanism for correlating internal data through UBA tools. Traditional tools and methods may not pick up on subtle behavioral indicators. This necessitates a more nuanced analysis that integrates multiple data sources.
Flashpoint provides advanced solutions that enhance insider threat detection and management. Flashpoint Ignite is designed to help organizations recognize the signs of insider behaviors and activity. It also monitors, analyzes, and responds to threat actor TTPs.
Identify Insider Threats Using Flashpoint
Insider threats represent a complex security challenge. It requires more than just technological solutions. It demands a strategic approach tailored to the nuanced dynamics of internal organizational environments. As threats evolve, so too must our strategies to counter them. This requires ongoing vigilance and adaptation. To better understand and combat insider threats within your organization, sign up for a demo today.
Frequently Asked Questions (FAQ)
Q: What defines an insider threat?
A: An insider threat is a risk to an organization’s security posed by people within the organization, such as employees or contractors, who have legitimate access to systems. This threat can be intentional (malicious) or unintentional (due to negligence or carelessness).
Q: Why is an insider threat difficult to detect?
A: Insiders are difficult to detect because they already possess legitimate access to critical systems, bypassing many traditional security defenses built to stop external threats. Detecting them requires sophisticated tools like User Behavior Analytics (UBA) and monitoring external sources for early warning signs like data being solicited online.
Q: How does Flashpoint help manage insider risk?
A: Flashpoint provides advanced visibility into external sources (deep and dark web forums) to detect indicators of insiders soliciting company data or access. This intelligence helps security teams recognize signs of insider activity, allowing for proactive analysis and response before a data breach or incident occurs.
Get the latest news and insights delivered to your inbox.
Want Flashpoint news delivered straight to your inbox? Subscribe to our newsletter for breaking news, expert analysis, essential guides, articles, videos, and more.
