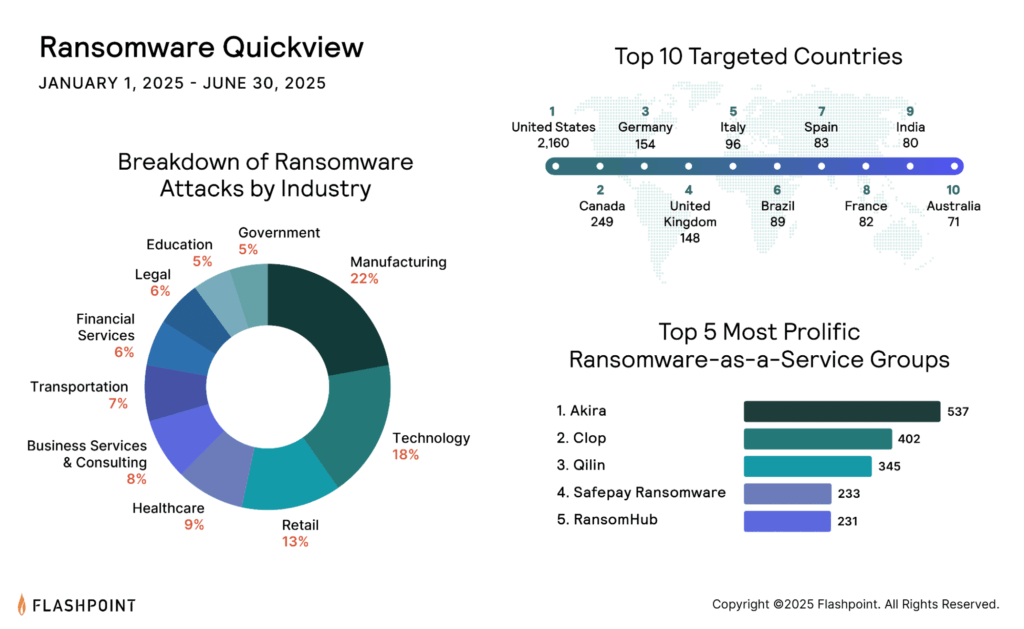
Despite significant advancements in cybersecurity defenses, ransomware continues to be one of the greatest financial and operational risks facing organizations worldwide—with Flashpoint finding that ransomware attacks increased by 179% compared to the 2024 midyear.
This continuous growth of ransomware is driven by ransomware-as-a-service (RaaS) operators and affiliates. In this post, we take a deeper look into the ransomware landscape, highlighting new emerging RaaS that every organization should be paying attention to in 2025.
The Rise and Fall of RaaS in 2025
Over the past year, Flashpoint has observed the emergence of multiple new RaaS groups. Some of these groups appear to have already shuttered or maintained blogs that are currently available.
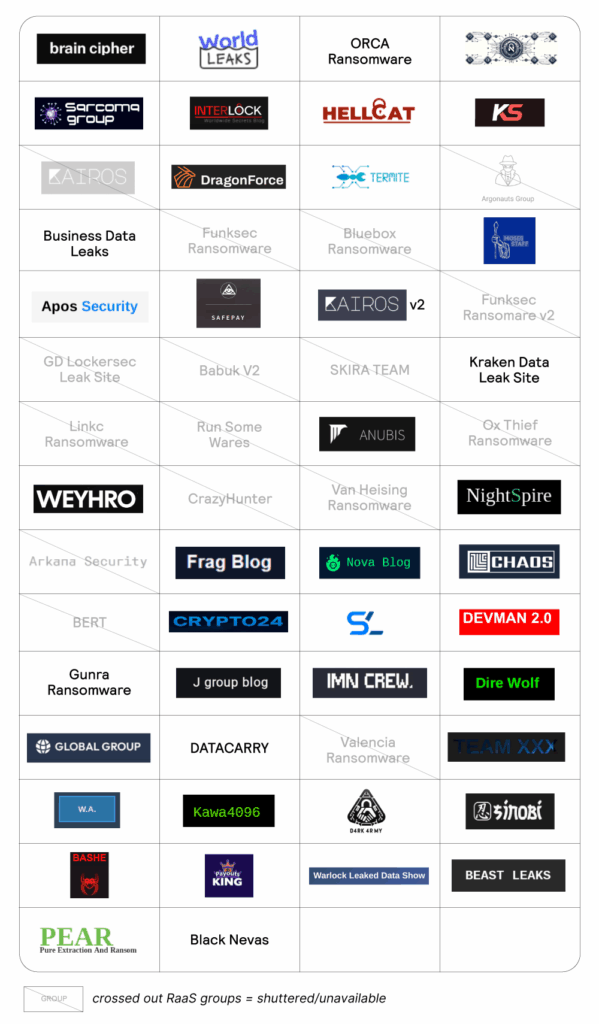
Outside of the top groups of ransomware groups, Akira, Clop, Qilin, Safepay, and RansomHub, there are several other groups that need to be watched. These groups are notable for their associations and some of their tactics, signaling a change in ransomware operations.
1. Extortion over Encryption
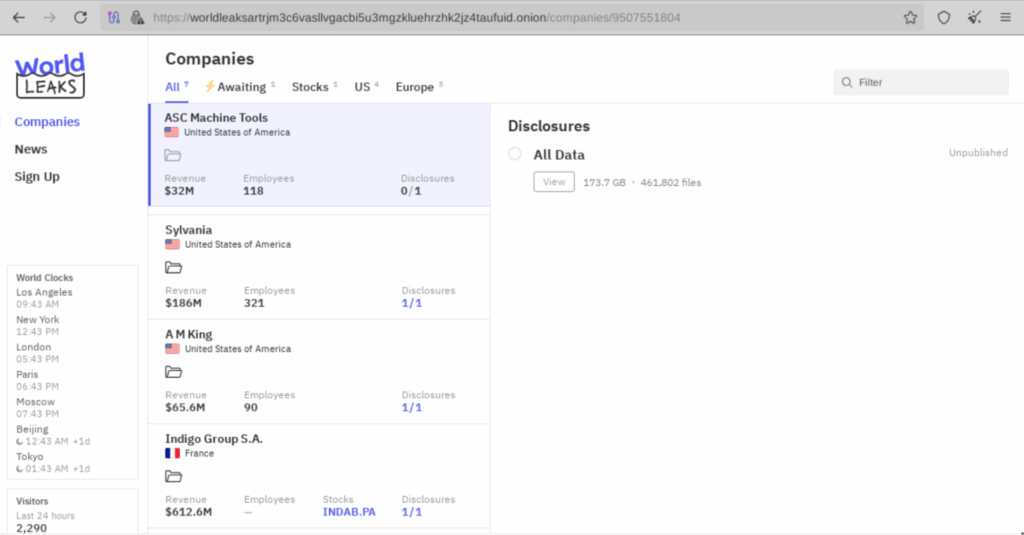
Multiple groups appear to prefer a pure extortion play. Ransomware groups will traditionally encrypt files before exfiltrating them, charging for both the decryption key and to prevent data from being leaked. Extortion groups like World Leaks, previously known as Hunter’s International, ransoms without encryption. Additionally, RansomHub has been observed occasionally employing this tactic, as well as emerging groups like Weyhro.
2. Family Ties
Ransomware rebranding is a known phenomena, where shuttered groups will often relaunch under a different name. Additionally, ransomware groups may also use leaked ransomware source code in their operations. For example, top ransomware group SafePay shares code with LockBit. The fingerprints of other notable ransomware groups, like Conti, are also apparent in the codebase of other ransomware groups. There is also overlap in other groups, like Devman and DragonForce.

3. AI Tooling
Funksec is one of the few groups openly using LLMs in their tooling. The group uses AI-generated phishing templates, and developed the malicious chatbot dubbed “WormGPT.” It is possible that additional groups will integrate the use of LLMs or chatbots within their operations in 2025.
4. What Is Old Is New Again
In January 2025, the shuttered ransomware group Babuk appeared to return as Babuk v2. Upon further analysis, the page appeared to be a group using the name notoriety of Babuk, and recycling previous ransomware victims from other ransomware groups. Data appearing on leak sites will often appear across other venues, like forums and Telegram channels, after the initial incident.
5. Access Vectors
While AI tooling may result in improved phishing campaigns, threat actors will continue to exploit disclosed but unpatched vulnerabilities, as well as infostealers as initial access vectors. Vulnerabilities in remote monitoring and management (RMM) remain targets for ransomware groups. Once access is gained, threat actors will often use Living off the Land (LOTL) techniques to escalate privileges.
Falling Off in 2025
While 2025 has introduced new RaaS into the ransomware landscape, it has also led to the downfall of others. Flashpoint has observed over 29 ransomware groups are no longer active going into 2025. However, while these illicit organizations are not currently operating, it does not mean that they are entirely gone—as it is common for RaaS groups to simply rebrand, reemerging as a new entity.
LockBit
For the past several years, LockBit has consistently been the most prolific RaaS operation, claiming over 3,500 victims since their first appearance in 2019. Now, the group is failing to even rank among the top fifteen most active ransomware groups—leading to the rise of other groups such as Akira.
Several factors have contributed to LockBit’s fall from grace; most notably global law enforcement action via Operation Cronos in February 2024 and subsequent sanctions against LockBit’s founder, Russian national Dmitry Yuryevich Khoroshev. Despite these events, LockBit managed to hold momentum through the remainder of 2024. However, the final blow to their operations occurred in May 2025, where an affiliate was breached and exposed key elements of the ransomware’s infrastructure. Flashpoint has not observed any new victim postings since May 9, 2025.
BlackCat (AKA Noberus / ALPHV)
2024 has marked the end of other notorious groups like the BlackCat ransomware collective, whose victim posts once rivaled LockBit and Clop. Known for its highly sophisticated ransomware and triple extortion model, the group was taken down by law enforcement in December 2023. The group relaunched and announced its official shutdown in March 2024. Since the shutdown, Flashpoint has not observed any new posting of BlackCat / ALPHV victims. Additionally, our analysts have found that many BlackCat affiliates have joined the newly formed RansomHub group.
Infiltrating threat actor communities, Flashpoint analysts sourced illicit communications claiming BlackCat itself was a rebranding of the once prominent Darkside / BlackMatter ransomware gang. This highlights a trend of continuous cybercrime where “defunct” RaaS operations are often not eliminated, instead reemerging or rebranding as a new entity.
Protect Against Ransomware Using Flashpoint
While the threat landscape is constantly evolving, the need for proactive and comprehensive defense remains the same. Staying ahead of cybercriminals and illicit marketplace trends requires comprehensive and actionable threat intelligence.
For a deeper dive into the trends that define today’s threat landscape, download Flashpoint’s 2025 Global Threat Intelligence Index. To see how Flashpoint’s real-time, human-curated, and AI-assisted intelligence can help your team counter ransomware groups, request a demo today.
Frequently Asked Questions (FAQs)
What are the top ransomware groups to watch in 2025 and how does Flashpoint Ignite track them?
The top ransomware groups to watch in 2025 include RansomHub, Cicada3301, and others within Flashpoint Ignite’s monitoring scope that are rapidly expanding their affiliate networks. Flashpoint Ignite tracks these groups by scraping their dedicated leak sites and monitoring illicit forums for recruitment ads and “teaser” data dumps. This allows organizations to identify which ransomware strains are currently the most active and which industries they are actively targeting.
| Ransomware Group | 2025 Strategic Focus | Flashpoint Ignite Benefit |
| RansomHub | High-payout affiliate models and data extortion. | Alerts you when your domain appears on their leak site. |
| Cicada3301 | Sophisticated encryption of Linux and ESXi systems. | Provides technical indicators for cloud and server defense. |
| New Affiliates | Exploiting zero-day flaws for initial access. | Tracks the sale of “access” on high-tier criminal forums. |
How does Flashpoint help organizations defend against “intermittent encryption”?
Flashpoint helps defend against intermittent encryption by providing technical analysis and file hashes for the latest ransomware variants. Because this method skips parts of a file to avoid detection by behavior-based antivirus, traditional monitoring may fail. Flashpoint’s malware intelligence gives security teams the specific “YARA rules” and signatures needed to detect these stealthy encryption patterns before they can lock down the entire network.
- Behavioral Analysis: Details how new 2025 strains avoid triggering security alerts.
- Malware Hashes: Provides the latest file signatures to update your EDR and antivirus.
- TTP Intelligence: Explains the specific scripts used by affiliates to trigger fast encryption.
Why is Flashpoint’s visibility into ransomware recruitment vital for 2025?
Flashpoint’s visibility into ransomware recruitment is vital because it reveals the intent and capabilities of the criminals carrying out the attacks. Most 2025 breaches are conducted by affiliates who rent the ransomware code. By monitoring the forums where these partners are recruited, Flashpoint identifies which “initial access” methods are currently in high demand, such as stolen VPN credentials or specific software exploits, allowing you to shore up those defenses before an attack begins.
| RaaS Component | Security Risk | Flashpoint Strategic Response |
| The Developer | Creates the complex Rust/Go encryption code. | Provides technical reverse-engineering of the malware. |
| The Affiliate | Finds the way into your network and steals data. | Monitors for the sale of your corporate access. |
| The Negotiation | Manages the ransom demands and data leaks. | Tracks the group’s communication style and payment success. |


