“Flashpoint is committed to continual innovation and growth. The company’s future outlook includes a clear strategic direction aimed at providing timely and actionable intelligence to government, LEA, and public and private sector organizations.
This support is essential to protect people, critical assets, and infrastructure from a wide range of physical and cybersecurity threats.”
Frost and Sullivan
Navigating a challenging year
Commercial enterprises and public sector organizations faced a diverse and complex threat landscape in 2023—a year marked by at least two major military conflicts and a ransomware campaign that impacted thousands of companies globally.
- The Israel-Hamas War, which began in October, continues into a second month despite a brief ceasefire. Russia’s invasion of Ukraine, meanwhile, continues into a second consecutive year. In Gaza, especially, a humanitarian crisis has emerged.
- One of 2023’s core cybersecurity challenges was the rise of supply chain attacks targeting software, coding packages, and third-party services, most notably illustrated by the ransomware group Clop, which weaponized zero-day vulnerabilities in file transfer services like GoAnywhere MFT and MOVEit to breach thousands of organizations.
Throughout the year, Flashpoint’s blogs, reports, op-eds, and media appearances aimed to drive valuable, data-rich insights into major stories affecting our clients and the greater intelligence community, without speculation. Here is a recap.
Related reading: 2023 Innovation Rewind: Top 10 Flashpoint Products, Features, and Developments
The Israel-Hamas War
Modern military conflicts are “fought” across both physical and digital domains, from on-the-ground combat to cyber and information warfare, where the battle for public opinion can become as crucial as territorial gains. The Israel-Hamas War poses crucial questions regarding the region’s future stability—especially when considering the intricate interplay of cyber, physical, and geopolitical security and intelligence challenges.
Our intelligence and insights on the war have always aimed to keep intelligence professionals, security experts, policymakers, and others informed as the conflict unfolds, leveraging our intelligence to deliver clarity amidst the chaos.
In the first 72 hours of the Israel-Hamas War, we analyzed Telegram’s role in facilitating communication and strategy for Hamas and PIJ during the initial 72 hours (3 days) of the conflict, beginning October 7.
We also zoomed out on cyber warfare in general, taking what we’ve seen thus far in the Israel-Hamas war, drawing parallels with the Russia-Ukraine war, and describing what is a playbook of sorts for cyber warfare in modern military conflicts.
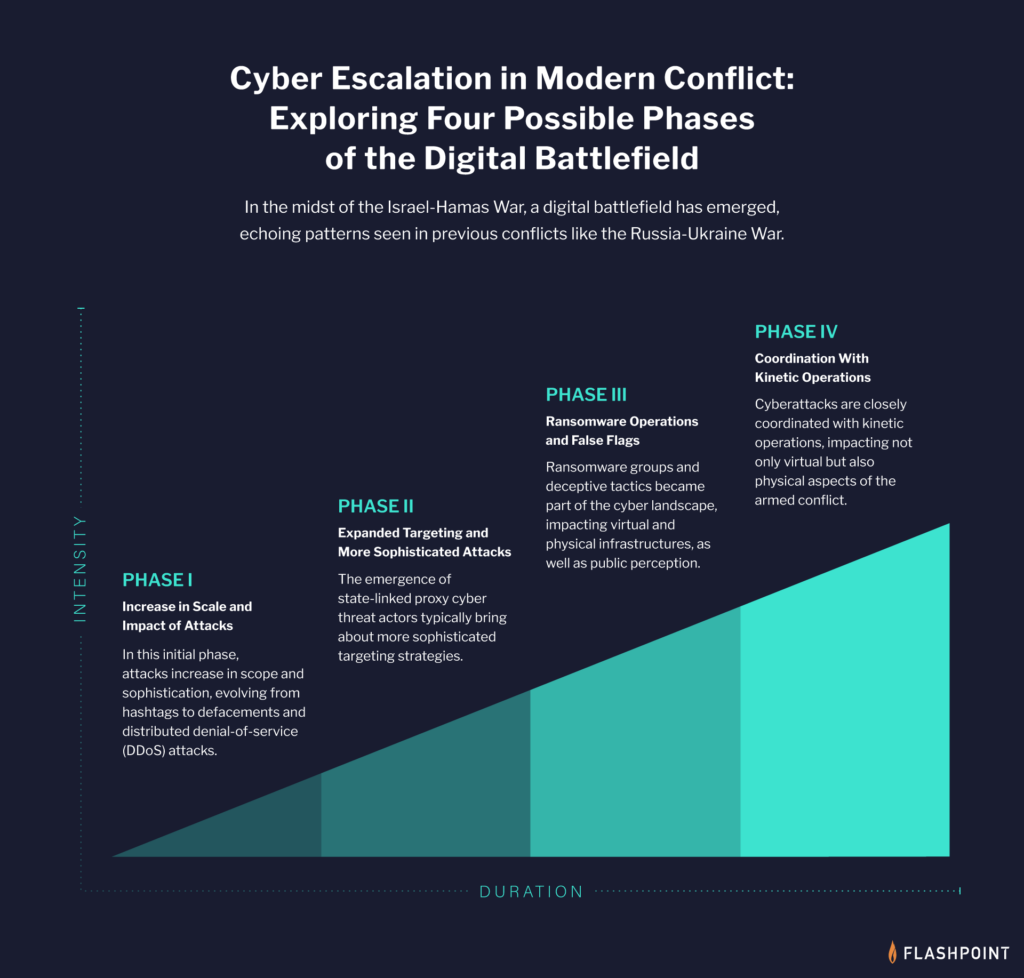
Commentary: Andrew Borene on the Israel-Hamas War
Andrew Borene, Executive Director of Flashpoint National Security Solutions, has served as our company spokesperson throughout the Israel-Hamas War, ranging from MSNBC, Bloomberg, Scripps and CNN, to Fox Business, Newsweek, CNBC, and USA Today.
Commentary: Russia, China
- A former senior intelligence official, Andrew Borene was also cited by Reuters following the reported death of Wagner Group leader Yevgeny Prigozhin in an August plane crash.
- In November, he also highlighted the escalating threat of Chinese espionage against Western democracies in this RUSI op-ed.
Commentary: Deftly navigating AI
In October, President Biden issued an Executive Order to enhance AI safety, privacy, fairness, consumer and worker protection, competitive ecosystem, and set international and governmental AI standards. To learn more about navigating the AI threat landscape, read our deep-dive guide about AI’s double-edged sword, from regulatory efforts to malicious exploits.
Earlier in the year, as ChatGPT and other generative AI applications took the world by storm, Flashpoint CEO Josh Lefkowitz penned an editorial for Context, the opinion page for Thomson Reuters, titled “ChatGPT is changing the game — but not without risks”.
OSINT, OSINT, OSINT
Earlier in the year, we published an in-depth report highlighting the role of open-source intelligence (OSINT) in understanding the Russia-Ukraine War following the one-year mark on the breakout of war.
Amid wide coverage of the insights it provides, Flashpoint analysts were included in two Newsweek features in February:
- The first focuses on how one Russian mercenary group was “openly competing with the Russian army for human resources.”
- The second details a viral video at the Kremlin of Russian President Vladimir Putin being told of significant problems regarding mobilization by Russia’s Prosecutor General Igor Krasnov.
Putting OSINT into action
At the beginning of the year we published our OSINT Tools Library—a continuously updated list of web-based OSINT tools and techniques from across the open-source intelligence community, curated by Flashpoint. This library has been listed as a notable resource by the Global Investigative Journalism Network.
Other resources
- This year we also launched the Flashpoint cybersecurity and intelligence glossary, an easy-to-use guide to important topics that serves as an entrypoint into even deeper research.
- We also launched our regular LinkedIn newsletter, The FLINT Report. Subscribe here.
Data, Data, Data: 2023 Edition
Early next year, we’ll publish the 2024 version of our annual State of Cyber Threat Intelligence report. Stay tuned. In the meantime, we have plenty of data-rich intelligence reports that provide a detailed overview of the cyber threat landscape from 2023.
- Click here to download 2023’s State of Cyber Threat Intelligence Report
- Click here to view or download our H12023 CTI Index
- Click here to view or download our Q3 CTI Index
Each of these reports provides insight into a number of security challenges across the cyber threat landscape, focusing in particular ransomware, malware, insider threat, vulnerabilities, and data breaches. Data derived from Flashpoint’s data breach intelligence was cited in a January Newsweek cover story.
Q3 CTI Index
Malware
- Our blog on the RisePro stealer, a version of which was for sale on an illicit marketplace, was widely cited: Security Week, Security Newspaper, SC Magazine, ITSecurityWire, Risky Biz News, Cywar, Bleeping Computer, Tech Spot, The Hacker News, Cyber News, and other publications.
- We also published a blog on Danabot Version 3.
- Flashpoint malware domain experts also provided commentary to Krebs on Security and The Record.
Clop
As of December 1, Clop‘s exploitation of the MOVEit vulnerability (CVE-2023-34362 (VulnDB ID: 322555) has affected 2,098 victims, according to our intelligence, which includes third-party victims that did not use MOVEit but whose data was exposed by a service provider.
In addition to publishing numerous blogs that added contextual value to a fast-moving threat, we also sat down with press to provide fresh perspective. This included speaking with Cybernews at Black Hat to chat about Clop ransomware and the cyber extortion economy.
H1 CTI Index: Midyear Report
Killnet
Our coverage of Killnet—both in terms of our intelligence- and data-driven blogs, as well as our media commentary about the group—has been consistent throughout 2023, which says a lot about the activity of the hacktivist group, especially in the first half of the year.
Here are a few notable 2023 blogs about Killnet, most of which focused on making sense of the group’s activity in relation to the Russia-Ukraine War.
- ‘Black Skills’ Is Killnet’s Attempt to Form a ‘Private Military Hacking Company’
- Making Sense of Killnet, Russia’s Favorite Hacktivists
- Killnet Ostracizes Leader of Anonymous Russia, Adding New Chapter to Pro-Kremlin Hacktivist Drama
Illicit communities and forums
2023 saw major changes in illicit communities while threat actors leveraged new tools and tried-and-true methods to carry out high-profile attacks. Here is a recap of our coverage of significant events, plus additional insights.
Breach Forums
Breach Forums, the successor to the now-defunct Raid Forums, saw several major events in 2023. In March, the site’s administrator, “pompompurin” (later identified as Connor Brian Fitzpatrick), was arrested and eventually pleaded guilty to cybercrime and child pornography charges.
Our intelligence on the arrest of the Breach Forums admin earned coverage in The Washington Post, The Hacker News, TechTarget, Computing, ISMG, and other publications.
AlphaBay
In early 2023, the second iteration of AlphaBay quietly shut down after the disappearance of its administrator, “DeSnake.” This kicked off a range of rumors regarding the fate of the market and DeSnake, who evaded the 2017 law enforcement action against the first AlphaBay.
Libre and Dread
In March, the popular English-language forum Dread came back online after several months of downtime due to persistent distributed DDoS attacks. Dread’s absence had a profound impact on its users and customers of Dark Web drug markets, as users were unable to share information about shops, vendors, and sellers. Similar forums such as Libre Forum emerged to fill the void.
Genesis Market
2023 saw the effective closure of Genesis Market following the seizure of its domains during “Operation Cookie Monster” and sanctioning by the US government in April. Our intel on Genesis Market was featured in Krebs on Security.
2easy and Russian Market
In The Record, Flashpoint analysts shared their expertise about Russian Market, 2easy Shop, and the general darknet marketplace landscape in an article titled, “Suspicion stalks Genesis Market’s competitors following FBI takedown.”
Get Flashpoint on your side
Flashpoint, the pioneering leader in threat data and intelligence, empowers commercial enterprises and government agencies to decisively confront complex security challenges, reduce risk, and improve operational resilience amid fast-evolving threats. Through the Flashpoint Ignite platform, we deliver unparalleled depth, breadth and speed of data from highly relevant sources, enriched by human insights—helping our customers safeguard critical assets, avoid financial loss, and protect lives and resources. Get a demo today.


