Blog
The Seven Phases of a Ransomware Attack: A Step-by-Step Breakdown of the Attack Lifecycle
Understanding the anatomy of a ransomware attack empowers security teams to strengthen defenses, reduce the risk of successful attacks, and protect organizations from the serious consequences of a ransomware incident

Ransomware attacks are pervasive and devastating, targeting organizations and causing havoc on operations, finances, and reputation. To defend against these threats, security teams must understand the ransomware attack lifecycle.
As reliance on digital systems and networks increases, the risk of ransomware attacks grows exponentially. These attacks can cripple businesses, disrupt services, compromise data, and lead to significant financial losses. Cybercriminals continually evolve their tactics, demanding constant adaptation from security teams.
In this blog, we will explore the intricacies of ransomware, breaking down the attack lifecycle. Understanding this anatomy empowers security teams to strengthen defenses, reduce the risk of successful attacks, and protect organizations from the serious consequences of a ransomware incident.
Phase 1: Reconnaissance and target selection
Phase 1 of a ransomware attack involves the threat actor researching and selecting organizations to attack. During this phase, threat actors identify potential targets and gather critical information about them.
Identifying potential targets
Threat actors engage in reconnaissance to identify organizations that are more likely to yield a high return on their malicious activities. They carefully assess factors such as the industry, size, financial stability, and the value of the data held by the potential targets. Organizations that heavily rely on their digital infrastructure and are more likely to pay a ransom to regain access to critical systems and data are prime targets.
Techniques used for reconnaissance
Threat actors employ various techniques to gather information during the reconnaissance phase. These techniques may include passive reconnaissance, where they collect publicly available data from websites, social media platforms, and professional networking sites. They may also utilize active reconnaissance, such as scanning for open ports and vulnerabilities, conducting phishing campaigns to gather employee information, or leveraging third-party sources like leaked databases and dark web forums.
Vulnerability factors
Several factors can make organizations more vulnerable to targeting during the reconnaissance phase:
- Lack of Security Awareness: Organizations that do not prioritize cybersecurity awareness and training for their employees may inadvertently provide attackers with valuable information through social engineering tactics.
- Inadequate Patch Management: Failure to promptly apply software patches and updates leaves systems vulnerable to known vulnerabilities that threat actors can exploit.
- Weak Access Controls: Poorly managed user accounts, weak passwords, and insufficient access controls increase the likelihood of unauthorized access to sensitive systems and data.
- Absence of Network Segmentation: If an organization’s network lacks proper segmentation, a successful initial access point can provide attackers with the opportunity to move laterally within the network and escalate privileges.
- Lack of Monitoring and Detection: Organizations that lack robust monitoring and detection capabilities may not notice the initial signs of a reconnaissance attempt, allowing threat actors to proceed undetected.
Phase 2: Initial access
Phase 2 of a ransomware attack is the critical stage where threat actors strive to gain initial access to an organization’s network and systems.
During this stage, threat actors employ a range of techniques to achieve initial access, including:
- Phishing Emails: One of the most common and successful methods, threat actors craft convincing emails designed to deceive recipients into clicking on malicious links or opening infected attachments.
- Exploit Kits: These toolkits contain prepackaged exploits that target vulnerabilities in software, commonly used web browsers, or plugins. By visiting compromised websites, unsuspecting users can unwittingly trigger the exploit kit and grant the attacker initial access.
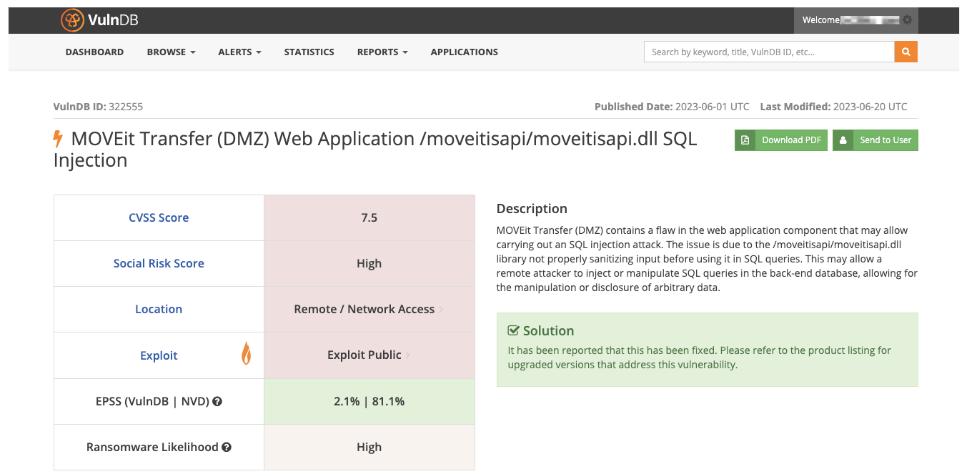
- Vulnerable Software: Exploiting weaknesses in software, particularly outdated or unpatched applications, is another avenue threat actors may exploit to gain a foothold within an organization’s network. This was recently observed through CLOP’s use of the MOVEit and GoAnywhere MFT vulnerabilities to attack over 100 organizations globally.
Social engineering tactics play a significant role in the success of initial access attempts. Threat actors exploit human psychology to deceive individuals and gain access to sensitive information or systems.
Pretexting, where a false scenario or pretext is created to gain the target’s trust, and baiting, which offers enticing rewards or incentives, are common social engineering tactics used to manipulate individuals. Moreover, tailgating—or taking advantage of individuals holding doors open for others—can be used to gain unauthorized physical access to secure areas within an organization.
Phase 3: Lateral movement and privilege escalation
Once threat actors have gained initial access to an organization’s network and systems, they proceed to Phase 3 of a ransomware attack: lateral movement and privilege escalation.
This stage involves the navigation and expansion of their reach within the compromised network. Threat actors explore the compromised network to locate valuable data, critical systems, and potential targets for encryption.
They employ lateral movement, traversing through the network to gain control over multiple machines, servers, or devices, which increases the likelihood of finding and encrypting valuable information while making it challenging for defenders to contain the attack.
Threat actors may use several techniques to achieve lateral movement.
- Exploiting Misconfigurations: They take advantage of misconfigured network shares, weak or shared passwords, and unsecured remote desktop protocols (RDP) to gain unauthorized access to other systems within the network.
- Credential Theft and Reuse: They employ various tactics to steal or acquire legitimate user credentials, such as using keyloggers, credential harvesting, or compromising administrative accounts. These stolen credentials are then reused to move laterally within the network.
- Pass-the-Hash: This technique involves stealing hashed credentials from compromised systems and using them to authenticate and gain access to other systems without needing to know the plaintext passwords.
Once within the network, threat actors seek to escalate their privileges. By elevating their access rights, they gain increased control over critical systems and can maneuver more freely within the network. Privilege escalation techniques may include:
- Exploiting Vulnerabilities: They identify vulnerabilities in software, operating systems, or network configurations that can be leveraged to elevate their privileges. This may involve exploiting unpatched systems or misconfigured permissions.
- Leveraging Stolen Credentials: If threat actors have successfully stolen credentials during the initial access phase, they can use these credentials to escalate their privileges within the network, gaining administrative or higher-level access.
- Abusing Trusted Applications or Services: They manipulate trusted applications or services that have higher privileges or access rights to gain elevated permissions within the network.
It is important to note that lateral movement and privilege escalation are not necessarily linear processes. Threat actors adapt their tactics based on the network’s topology, security measures, and available targets, maneuvering opportunistically within the network.
Phase 4: Deployment of ransomware payload
In Phase 4 of a ransomware attack, threat actors execute their ultimate objective: deploying the ransomware payload. This phase involves the encryption of the victim’s files and the subsequent demand for a ransom payment.
Ransomware comes in various forms, each with its own characteristics and objectives. Some common types include:
- Encryption Ransomware: This type of ransomware encrypts the victim’s files, rendering them inaccessible until a decryption key is obtained by paying the ransom. Examples include notorious strains like WannaCry and Ryuk.
- Locker Ransomware: Locker ransomware locks the victim out of their system or specific applications, denying access to the device or critical functionalities. It often displays a ransom message directly on the victim’s screen, demanding payment to regain access.
- Hybrid Ransomware: Hybrid ransomware combines elements of both encrypting and locker ransomware. It encrypts files while simultaneously locking the victim out of the system, amplifying the impact and urgency of the attack.
To deploy the ransomware payload effectively, threat actors may leverage various techniques including:
- Email Attachments and Links: Malicious attachments or links embedded within phishing emails are a common delivery method for ransomware. Opening the attachment or clicking on the link initiates the download and execution of the ransomware payload.
- Drive-by Downloads: By visiting compromised or malicious websites, victims unknowingly trigger the download and execution of ransomware through vulnerabilities in their web browsers or plugins.
- Exploit Kits: Exploit kits can exploit vulnerabilities in software or operating systems to deliver ransomware onto the victim’s system. The kits automatically detect and target vulnerabilities, enabling threat actors to distribute the ransomware payload more efficiently.
Ransomware-as-a-Service (RaaS) and its role in the attack lifecycle
Ransomware-as-a-Service (RaaS) has emerged as a significant contributor to the proliferation of ransomware attacks. RaaS allows less technically skilled threat actors to access ransomware tools and infrastructure developed by more sophisticated actors. It operates on a profit-sharing model, where the developers take a percentage of the ransom payments. RaaS lowers the barrier to entry for cybercriminals, enabling the widespread distribution and execution of ransomware attacks.
Recommended Reading: The History and Evolution of Ransomware Attacks
RaaS platforms provide aspiring threat actors with user-friendly interfaces, technical support, and even customer service. They often offer customization options, allowing attackers to tailor the ransomware to their specific targets. The availability of RaaS has led to a surge in ransomware attacks globally, as it empowers a wider range of cybercriminals to participate in these lucrative campaigns.
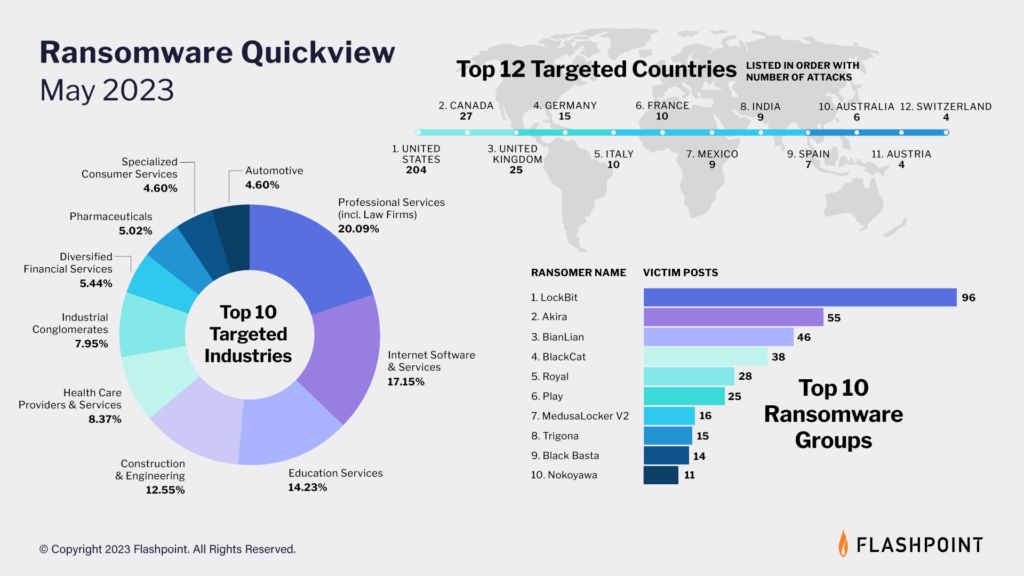
Phase 5: Encryption and impact
The true consequences of the attack begin to unfold during the encryption and impact phase. During this phase, threat actors encrypt the victim’s files and inflict significant damage on their systems.
Ransomware employs sophisticated encryption algorithms to lock the victim’s files, rendering them inaccessible without the decryption key. The encryption process typically targets a wide range of file types, including documents, images, videos, databases, and more. Threat actors often use strong encryption algorithms like RSA or AES to ensure the victim cannot decrypt the files without the decryption key.
As the encryption process unfolds, the victim’s files become unusable, with each file typically receiving a unique encryption key. The ransomware may also overwrite or modify the original file, making recovery without the decryption key even more challenging. The impact on the victim’s systems can be severe, leading to operational disruption, data loss, financial consequences, and reputational damage.
The consequences of a successful ransomware attack can be devastating for both organizations and individuals, and often entails many of the following:
- Operational Disruption: Ransomware attacks can cripple an organization’s operations, causing significant disruptions and downtime. Critical systems may become inaccessible, leading to productivity losses, delayed services, and financial repercussions.
- Data Loss and Corruption: If proper backups are not in place, victims may lose access to their valuable data permanently. Ransomware may also corrupt files during the encryption process, making recovery even more challenging.
- Financial Losses: Organizations may face substantial financial losses due to ransom payments, costs associated with recovery and remediation efforts, and potential regulatory penalties. Moreover, there may be indirect financial impacts stemming from reputational damage and customer loss.
- Reputational Damage: Publicly disclosed ransomware attacks can tarnish an organization’s reputation. Clients, partners, and stakeholders may lose trust in the organization’s ability to protect sensitive information, leading to a loss of business opportunities and customer confidence.
- Legal and Regulatory Ramifications: Depending on the nature of the compromised data, organizations may face legal and regulatory consequences, especially if personal or sensitive information is involved. Violations of data protection regulations can result in significant fines and legal liabilities.
Phase 6: Extortion and communication
In Phase 6 of a ransomware attack, threat actors establish communication with their victims and begin the process of extortion. At this time, they’ll demand ransom payments in exchange for providing the decryption keys or access to the victim’s systems.
During this phase, threat actors initiate contact with the victim to convey their demands and establish a line of communication. They often use anonymizing technologies, such as the Tor network, to mask their identities and make it difficult to trace their activities. Communication can occur through various channels, including email, instant messaging platforms, or even dedicated ransom negotiation portals set up by the attackers.
Threat actors employ different methods to demand ransom payments from their victims. These may include:
- Bitcoin or Cryptocurrency Payments: Threat actors typically demand ransom payments in cryptocurrencies, such as Bitcoin, due to the pseudonymous and decentralized nature of these currencies, which makes them difficult to trace.
- Payment Deadlines and Threats: Threat actors often impose strict deadlines for payment, accompanied by threats of permanently deleting the decryption keys or increasing the ransom amount if the deadline is not met. These tactics aim to pressure victims into complying with their demands.
- Proof of Data Exfiltration: In some cases, threat actors may claim to have exfiltrated sensitive data from the victim’s systems and threaten to publicly release it unless the ransom is paid. This adds an additional layer of pressure and urgency for victims to comply.
Engaging or not engaging with threat actors during the extortion phase raises legal and ethical considerations. Organizations must carefully evaluate their options:
- Legal Considerations: Paying the ransom may be illegal in some jurisdictions or against organizational policies. Additionally, organizations may have legal obligations to report the incident, particularly if personal or sensitive data has been compromised.
- Funding Criminal Activities: Paying the ransom may contribute to funding further criminal activities, as the money can be used to finance future attacks. Supporting cybercriminals through ransom payments perpetuates the ransomware ecosystem.
- No Guarantee of Decryption: There is no guarantee that threat actors will provide the decryption keys or restore access to the victim’s systems even after the ransom is paid. Organizations must consider the risk of paying the ransom and not receiving the promised outcome.
- Cyber Insurance Coverage: Organizations with cyber insurance policies should consult with their insurance providers regarding their coverage and the implications of paying the ransom.
It is crucial for organizations to consult legal counsel, law enforcement agencies, and experienced incident response professionals before making any decisions regarding ransom payment. Each situation is unique, and a thorough evaluation of the risks, legal obligations, and ethical considerations is necessary.
Phase 7: Recovery and mitigation
The recovery and mitigation phase of an attack is where organizations focus on restoring systems, recovering encrypted data, and implementing measures to prevent future attacks.
Recovering from a ransomware attack requires a systematic approach. Key strategies for recovering encrypted data and restoring systems include:
- Isolate and Contain: Immediately isolate the affected systems to prevent further spread of the ransomware. Disconnect compromised devices from the network and shut them down to mitigate the risk of re-infection.
- Incident Analysis: Conduct a thorough analysis of the incident to identify the ransomware variant, its impact, and the compromised systems. This analysis can help determine the appropriate recovery strategy.
- Data Restoration: If backups are available, restore data from clean and secure backups. It is crucial to ensure backups are offline or properly protected to prevent them from being compromised by the ransomware.
- Decrypting Data: In some cases, decryption tools may be available from trusted sources, such as law enforcement agencies or security companies. These tools can help decrypt files without paying the ransom. However, this is not always possible, depending on the specific ransomware variant.
- System Rebuilding: In situations where data restoration is not feasible or backups are unavailable, organizations may need to rebuild affected systems from scratch using known good configurations and software.
Effectively responding to ransomware incidents requires a well-defined incident response plan, and may include some of these best practices:
- Incident Response Plan: Develop a comprehensive incident response plan that outlines the steps to be taken in the event of a ransomware attack. This plan should include roles and responsibilities, communication protocols, and predefined actions for different scenarios.
- Rapid Response: Ensure you have the alerting capabilities to act swiftly and decisively to contain the attack, isolate affected systems, and initiate the recovery process. Promptly engage internal IT teams, incident response experts, and relevant stakeholders.
- Communication and Notification: Establish clear lines of communication both internally and externally. Notify appropriate personnel, such as legal, PR, and executive teams, and consider legal and regulatory obligations for disclosing incidents involving compromised data.
- Forensic Investigation: Conduct a thorough forensic investigation to understand the root cause, identify the attack vector, and collect evidence for potential legal actions or future prevention measures.
- Employee Awareness and Training: Continuously educate employees about the risks of ransomware, phishing, and social engineering. Regularly train staff on cybersecurity best practices, including strong password management, recognizing suspicious emails, and reporting incidents promptly.
Prevention is key in mitigating future ransomware attacks. Implementing proactive security measures can significantly reduce the risk and impact of such incidents. Consider these important measures:
- Patch Management: Regularly apply security patches and updates to operating systems, software, and firmware to address known vulnerabilities that threat actors often exploit.
- Endpoint Protection: Deploy robust antivirus and anti-malware solutions, along with advanced endpoint detection and response (EDR) tools to detect and block malicious activities.
- Network Segmentation: Implement network segmentation to restrict lateral movement and contain the impact of an attack. Separating critical systems from the rest of the network helps prevent the rapid spread of ransomware.
- Least Privilege Access: Enforce the principle of least privilege, granting users only the necessary access rights required to perform their duties. This minimizes the potential damage that can be caused by compromised accounts.
- Regular Data Backups: Maintain regular, encrypted, and secure offline backups of critical data. Regularly test the restoration process to ensure backups are viable for recovery in the event of a ransomware incident.
Know your enemy
Ransomware attacks continue to evolve, becoming more sophisticated and widespread. Threat actors adapt their tactics, techniques, and tools to exploit vulnerabilities and maximize their financial gain. As such, ongoing vigilance and adaptation are essential.
But at each stage of a ransomware attack, robust threat intelligence can stop an emerging risk in its tracks and minimize—or even prevent—damage to your organization.
An effective threat intelligence program enables you to understand threat actors and their TTPs each step of the way. Critical capabilities for your threat intelligence program include:
- Vulnerability intelligence that gives practitioners access to real-time, comprehensive information so that they can understand the scope of the incident and develop effective response strategies to make faster, informed decisions and mitigate the attack.
- A robust alerting system that allows security practitioners o set up customizable, automated ransomware alerts of leaked assets as a result of an extortion incident, and gain insight into the extent of exposure and damage.
- Real-time and continuous data collection that includes background and assessments of the vulnerability, status updates with timelines, known victims, change logs, and intelligence that contributes to a more holistic understanding of a risk and informs decision-making.
- A managed attribution solution that allows intelligence teams to shift from defense to offense by enabling security teams to safely and anonymously conduct investigations.
- Robust risk management practices and incident response plans in place in order to respond effectively and recover from security breaches.
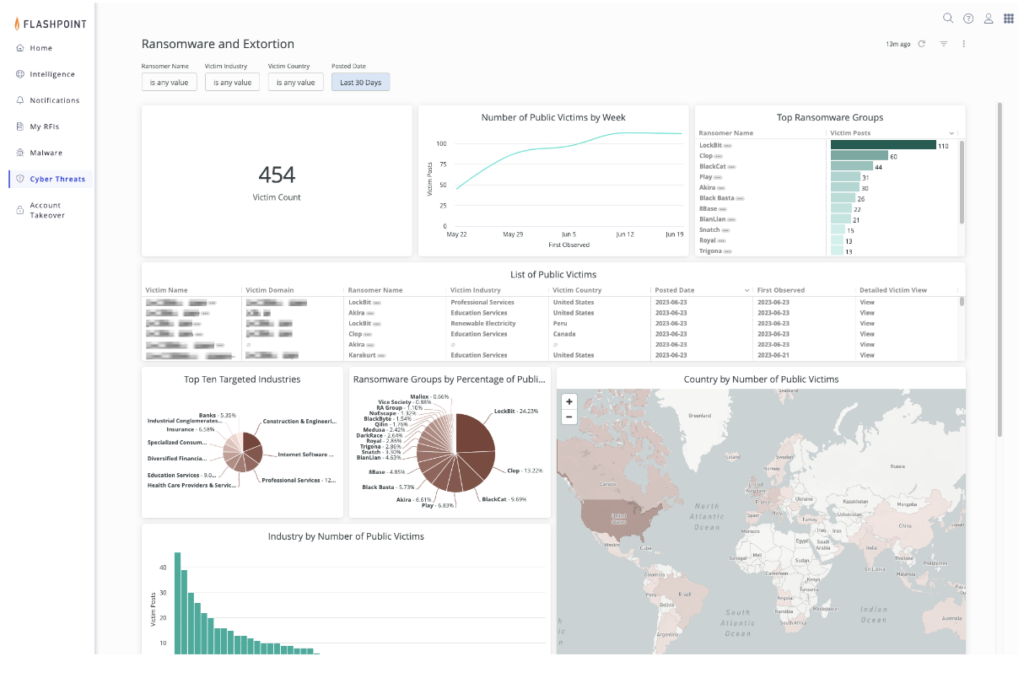
To learn more about how Flashpoint empowers security teams to prevent and respond to ransomware attacks, begin a free trial, or watch this video to discover the top ways to prevent an attack at your organization.

