Blog
Protecting Critical Infrastructure: The Intersection of Industrial Control Systems and Threat Intelligence
Organizations operating with industrial control systems are uniquely positioned within the threat landscape—and defending them has never been more critical.

In April 2022, Conti Ransomware commenced an attack on nearly 30 Costa Rican government institutions. They claimed that nearly a terabyte of personal and financial data from thousands of citizens and organizations had been stolen.
The result: Disruptions lasting over a month, during which the newly-inaugurated Costa Rican president declared a state of national emergency. Several governmental branches’ operations were suspended, and millions of people relying on dozens of critical sectors were forced to wait.
The 2022 FBI Internet Crime Report emphasized the severity of cyberattacks, including ransomware events, against critical infrastructure. Over a third of ransomware attacks reported last year targeted critical infrastructure, and 14 of the 16 defined critical infrastructure sectors experienced attacks.
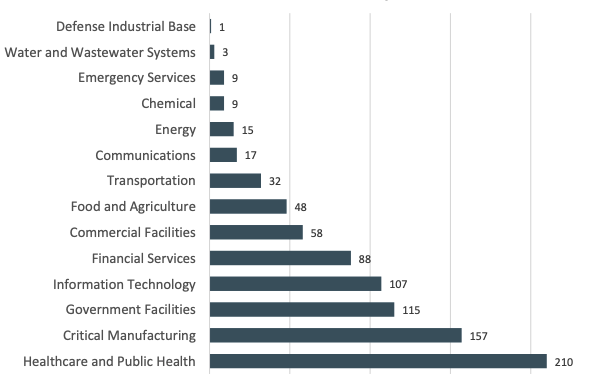
Flashpoint’s Cyber Threat Intelligence Index—which tracks five critical threats to organizations, including ransomware, insider threats, and vulnerabilities—also observes this trend. Organizations within the IT, Telecom, and Construction & Engineering sectors are frequently among the most targeted by various attack types.
Protecting these organizations is vital. And to understand the full scope of challenges that they face, it’s necessary to take a closer look at the systems that constitute them. Organizations operating with industrial control systems (ICS) are uniquely positioned within the threat landscape, and as such, tailored, proactive threat intelligence is a vital part of defending them.
In this blog, we’ll examine the distinct threats ICS organizations face, highlight the importance of threat and vulnerability intelligence in defending critical infrastructure, especially those operating with ICS, and offer practical strategies for doing so effectively.
And for a deeper dive, Flashpoint’s SVP of Customer Success and Chief Innovation Officer will be co-hosting a webinar that looks at the ICS risk landscape and steps teams can take to enhance their security. Sign up here.
The draws of ICS organizations
Why are critical infrastructure organizations, and specifically, those that operate using industrial control systems, so heavily targeted by threat actors?
For one, the price is right.
The significance of ICS cannot be overstated within critical infrastructure industries. These systems form the backbone of sectors including manufacturing, energy generation and distribution, and transportation networks. Their uninterrupted operation is essential for the functioning of society, the economy, and public welfare.
Disruptions to these systems can have severe consequences, so when an attack occurs, victim compliance may be more likely. When the Colonial Pipeline was attacked in May 2021, The Colonial Pipeline Company, overseen by the FBI, paid the equivalent of over $4 million in bitcoins within hours of the ransom being demanded—although approximately $2.3 million of this was later recovered by law enforcement.
For ideologically motivated or government/state-sponsored threat actors, the chaos and consequences—like financial losses, infrastructure damage, environmental impacts, and risks to public safety— that come with attacking these vital sectors is the end goal.
And for others, it’s simply a matter of the opportunity being there. There are several aspects of industrial control systems that make them especially prone to the possibility of an attack, and if security teams don’t implement measures to defend them, threat actors will take advantage.
ICS threat vectors
- Legacy systems and compatibility: Many ICS components and infrastructure were designed and implemented before the prevalence of modern cybersecurity standards. This legacy equipment often lacks built-in security features and can be challenging to integrate with newer technologies.
- Interconnectivity and exposure: The increasing interconnectivity of ICS systems with corporate networks and the internet exposes them to a broader range of cyber threats. This expanded attack surface makes them attractive targets for adversaries seeking to disrupt operations, compromise data integrity, or gain unauthorized access.
- Long lifecycles and patching: ICS components often have extended lifecycles and limited opportunities for frequent software updates or security patches. This characteristic makes it challenging to find actionable vulnerability intelligence on possibly susceptible ICS components, as well as to become aware of and address newly discovered vulnerabilities.
- Limited security expertise: ICS environments often require specialized knowledge and skills to implement robust security measures. The shortage of professionals with expertise in both industrial control systems and cybersecurity poses a significant challenge for organizations.
Risks and consequences of cybersecurity incidents
Security incidents within ICS can have severe consequences, impacting operations, safety, and overall business continuity.
- Disruption of Operations: Cyber attacks on ICS can disrupt critical processes, leading to production shutdowns, supply chain interruptions, and financial losses.
- Compromise of Safety: The exploitation of ICS security can compromise the safety of personnel, the public, and the environment. Adversaries may exploit vulnerabilities to manipulate control systems, creating hazardous conditions that could cause serious physical harm.
- Data Integrity and Confidentiality: Attacks on ICS can result in data manipulation, alteration, or theft. This compromises the integrity of operational data, undermines decision-making processes, and may lead to loss of confidential information.
- Reputational and Regulatory Impact: A cybersecurity incident affecting ICS can tarnish an organization’s reputation and erode customer trust. Regulatory authorities may impose fines, penalties, or compliance requirements, further impacting operations and resources.
The intersection of industrial control systems and threat intelligence
ICS organizations face distinctive security challenges, stemming from the convergence of operational technology (OT) and information technology (IT) environments. To effectively address these challenges, a comprehensive and customized approach becomes imperative.
Tailored threat intelligence plays a critical role in fortifying ICS protection, empowering organizations to proactively detect and counter emerging threats, vulnerabilities, and attack campaigns. By prioritizing threat intelligence, organizations can bolster their incident response capabilities, improve risk management strategies, and foster a culture of proactive security.
Beyond just providing information, effective ICS-specific threat intelligence emphasizes delivering timely and actionable insights. Such a proactive approach enables organizations to stay ahead of the curve by identifying emerging threats, zero-day vulnerabilities, and ongoing attack campaigns.
By harnessing the power of tailored threat intelligence, organizations can stay one step ahead in safeguarding their ICS infrastructure and proactively mitigating potential risks. This comprehensive and proactive strategy reinforces the resilience of ICS systems, ensuring the protection of critical assets and operations.
Benefits of threat intelligence for ICS
Leveraging threat intelligence provides numerous advantages for organizations aiming to enhance their ICS security posture.
Proactive threat detection
Threat intelligence enables proactive detection of potential threats by monitoring indicators of compromise, anomalous activities, and malicious patterns specific to ICS environments. This early warning allows organizations to respond swiftly and prevent or minimize damage.
Improved incident response
Threat intelligence enriches incident response capabilities by providing up-to-date information on threat actors, their tactics, and tools. This knowledge enables organizations to develop effective response strategies, contain incidents promptly, and recover systems efficiently.
Enhanced risk management
Incorporating threat intelligence into risk management processes allows organizations to prioritize risks based on their potential impact and likelihood. This informed approach enables the allocation of resources and implementation of countermeasures that address the most critical risks.
Strategic decision-making
Threat intelligence offers insights that aid in strategic decision-making. It helps organizations evaluate technology investments, assess the effectiveness of security controls, and develop long-term security strategies to protect ICS environments.
Practical strategies for enhancing ICS protection
To maximize the benefits of threat intelligence, organizations can implement several practical strategies to enhance their ICS protection.
- Continuous Threat Monitoring: Establish a robust threat monitoring program that leverages threat intelligence feeds, security information and event management (SIEM) systems, and intrusion detection/prevention systems to actively monitor ICS networks for potential threats.
- Vulnerability Assessments: Conduct regular vulnerability assessments to identify weaknesses in ICS components, networks, and applications. A comprehensive source of vulnerability intelligence gives security teams access to over 325,000 vulnerabilities containing the latest actionable metadata. And by combining this with threat intelligence, security teams can achieve a holistic view of their potential risk profile.
- Incident Response Planning: Develop comprehensive incident response plans that incorporate threat intelligence. Define roles, responsibilities, and communication channels to ensure swift and coordinated response actions in the event of a cybersecurity incident.
- Employee Training and Awareness: Provide targeted training and awareness programs to employees regarding ICS-specific threats and best practices. Educate personnel on social engineering techniques, phishing attacks, and safe computing practices to minimize the human factor in security incidents.
From risk to resilience
For deeper insights into the challenges faced by ICS organizations and practical strategies to enhance protection, join our upcoming webinar. We’ll address the complex landscape of operating industrial control systems and provide strategies to strengthen your protection. We’ll also explore the significance of unified vulnerability management, and offer strategies to empower ICS security teams with limited resources.


