Lessons from Clop
It’s been one month since the Clop ransomware group began exploiting the MOVEit vulnerability (CVE-2023-34362 (VulnDB ID: 322555) to claim nearly 100 victims across the globe, many of which have come public. This attack comes on the heels of Clop leveraging the GoAnywhere MFT vulnerability (CVE-2023-0669), which led them to claim they’d illegally obtained information for more than 100 companies.
When a ransomware or cyber extortion event occurs, security teams are racing against the clock:
- What do we know about the cybercriminal group that’s claiming responsibility for an attack or double extortion?
- Is our organization affected? If so, what is the extent of the breach and its impact on our systems, networks, people, and data?
- How do we respond to and mitigate the situation?
These questions are of vital importance to organizations across the public and private sectors. And the recent Clop attacks—which affected organizations across the globe in nearly every vertical—are yet another example of why it’s vital to have proactive defense measures in place.
Targeting upstream data providers
First, it’s vital to have a deep understanding of the adversary, such as a RaaS (ransomware-as-a-service) group like Clop. Here are five ways that ransomware groups like Clop attack targets, as well as the threat vectors they seen to exploit:
- Supply chain attacks. As illustrated through MOVEit, Clop often targets upstream software vendors or service providers so that it can cast a wide net. A number of the known Clop victims are companies who were attacked via a third-party vendor. Attackers like Clop may exploit vulnerabilities in the communication or data exchange between these companies, or compromise the software or hardware components supplied by third-party providers to inject malicious code or backdoors.
- Cloud Service Providers (CSP). If a cloud service provider experiences a security breach, it can potentially impact third parties that utilize their cloud services in several ways. Clop successfully breached a cloud service provider, giving them potential access to highly sensitive information.
- Managed Service Providers (MSPs), who inherently have access to clients’ IT infrastructure, are also a lucrative target for ransomware groups like Clop as they service a multitude of businesses.
- Software vulnerabilities are common, as ransomware groups often exploit known vulnerabilities in widely used software. Here, Clop exploited MOVEit, a file transfer software used by organizations globally, to install a malicious web shell called LEMURLOOT.
- Zero-days. Ransomware groups may also exploit zero-day vulnerabilities, or previously unknown security flaws, in software leveraged by a wide range of organizations.
Putting vulnerabilities into context
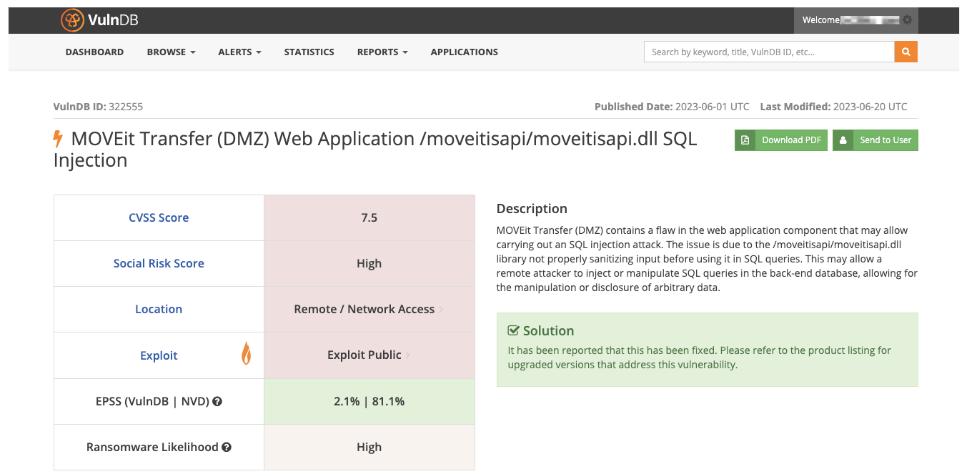
CLOP’s use of the MOVEit and GoAnywhere MFT vulnerabilities provide us with two recent high-profile examples of the power and impact of the group’s attacks—as well as the damage they can have on victims.
It also shines a bright light onto the level of information and context that CTI analysts and vulnerability management teams require in order to better prioritize and take action on the vulnerabilities likely to be used in ransomware and other attacks.
Tools such as Flashpoint’s VulnDB can unpack vulnerabilities like MOVEit in order to provide practitioners with access to real-time, comprehensive information so that they can understand the scope of the incident and develop effective response strategies to make faster, informed decisions and mitigate the attack.
This includes information about 300,000 vulnerabilities, including thousands not listed in the public source, as well as robust metadata and numerous prioritization and prediction metrics, including:
- a CVSS score
- social risk score
- EPSS score
- ransomware likelihood score
- supplemental information on which versions of software may be affected
Furthermore, when equipped with this context, vulnerability practitioners should be able to gain an active understanding of how the software, services, and other third-party assets they use are affected.
Alerting for faster awareness and remediation
Speed is crucial when responding to or setting up defenses for a ransomware or cyber extortion event. In order to stay current on known exploits and better understand potential organization risks, vulnerability managers, analysts, and researchers should be able to set up customizable, automated ransomware alerts of leaked assets as a result of an extortion incident, and gain insight into the extent of exposure and damage.
The combination of threat intelligence and vulnerability intelligence is a powerful weapon against adversaries. For instance, when a ransomware event occurs, vulnerability practitioners should be able to easily raise their awareness levels by using a robust alerting system. From there, they can quickly drill down into supplemental information to identify if exploits are being shared, see which threat actors are discussing the vulnerability across all illicit and open-source communities (forums, chats, ransomware sites, paste sites, blogs, social media, e.g.), and better assess the risk.
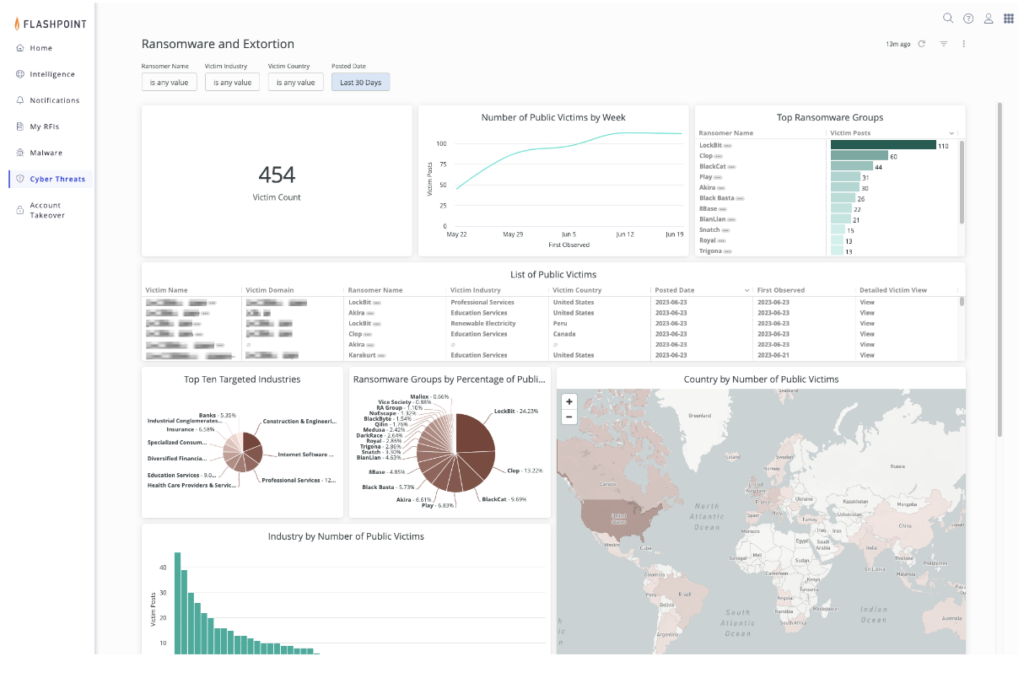
Understanding incidents as they unfold
Gaining continuous intelligence and context on ransomware attacks is vital throughout an attack, which often extends for weeks in the public sphere (and undoubtedly longer behind closed doors). It is therefore important to ensure that your organization is being provided with an active understanding of the situation as it unfolds in real-time—beyond vulnerability intelligence.
Flashpoint’s Intelligence Team, for example, delivers to customers incident pages and regular updates that communicate the most important details of an extortion event in progress. This includes background and assessments of the vulnerability, status updates with timelines, known victims, change logs, and intelligence that contributes to a more holistic understanding of a risk and informs decision-making.
Managed attribution for investigations
A managed attribution solution allows intelligence teams to shift from defense to offense by enabling security teams to safely and anonymously conduct investigations. Analysts will often access or download files from a ransomware blog to verify if their organization was impacted in the incident. While doing so, it’s vital to protect and keep your organization safe via a secure research environment that is isolated from analyst browsers, computers and network infrastructure. Flashpoint’s Managed Attribution solution allows security teams to interact with files, conduct online investigations, and browse safely without risk to their organization.
Ransomware response and readiness
To quickly assess, contain, and mitigate the impact of such incidents, it is crucial for organizations to have robust risk management practices in place. This includes conducting thorough due diligence when selecting third-party vendors, assessing their security practices, actively monitoring their security posture, and implementing contractual obligations and security controls to protect the company’s interests.
Additionally, it’s crucial to have incident response plans in place in order to respond effectively and recover from security breaches.In the event that an organization is impacted by ransomware, having a well-practiced incident response plan can greatly minimize damages. This includes:
- Creating an Incident Response playbook
- Holding mandatory training sessions for employees
- Enabling staff members to proactively thwart attacks
Ransomware and cyber extortion events are undoubtedly stressful and challenging, but there are practical and proven ways to lessen that burden to reduce risk across your organization. To learn more about how Flashpoint empowers security teams to prevent and respond to ransomware attacks, contact us, sign up for a free trial, or watch this video to understand the top ways to prevent a ransomware attack at your organization.


