GLOSSARY
What Are “Logs” and Their Importance in Cybersecurity
Login credentials, most commonly referred to as “logs,” are an umbrella term for any information that can be used to log in to an account. Logs frequently consist of a username and password pair. The term often refers to credentials obtained from botnets, but can also refer to login information obtained from dumps, leaks, or breaches.
Logs record a vast array of events and activities that occur within a network or on a specific device. From system operations to user activities, log files serve as a comprehensive record that can be crucial for troubleshooting, compliance, and security purposes. However, in the hands of threat actors, logs can give attackers much-needed information to exploit their target’s systems. As such, logs are an essential component for maintaining the integrity and security of information systems.
What are logs?
In cybersecurity, logs refer to login credentials—an umbrella term for any information that can be used to log in to an account. These frequently consist of a username and password pair. Logs can originate from various sources, including botnets, dumps, or data breaches. They are also commonly advertised and sold on Telegram channels, subscription log services, and illicit marketplaces. Therefore, it is critical that organizations monitor these sources for any potential listings affecting themselves or affiliated third-parties or contractors.
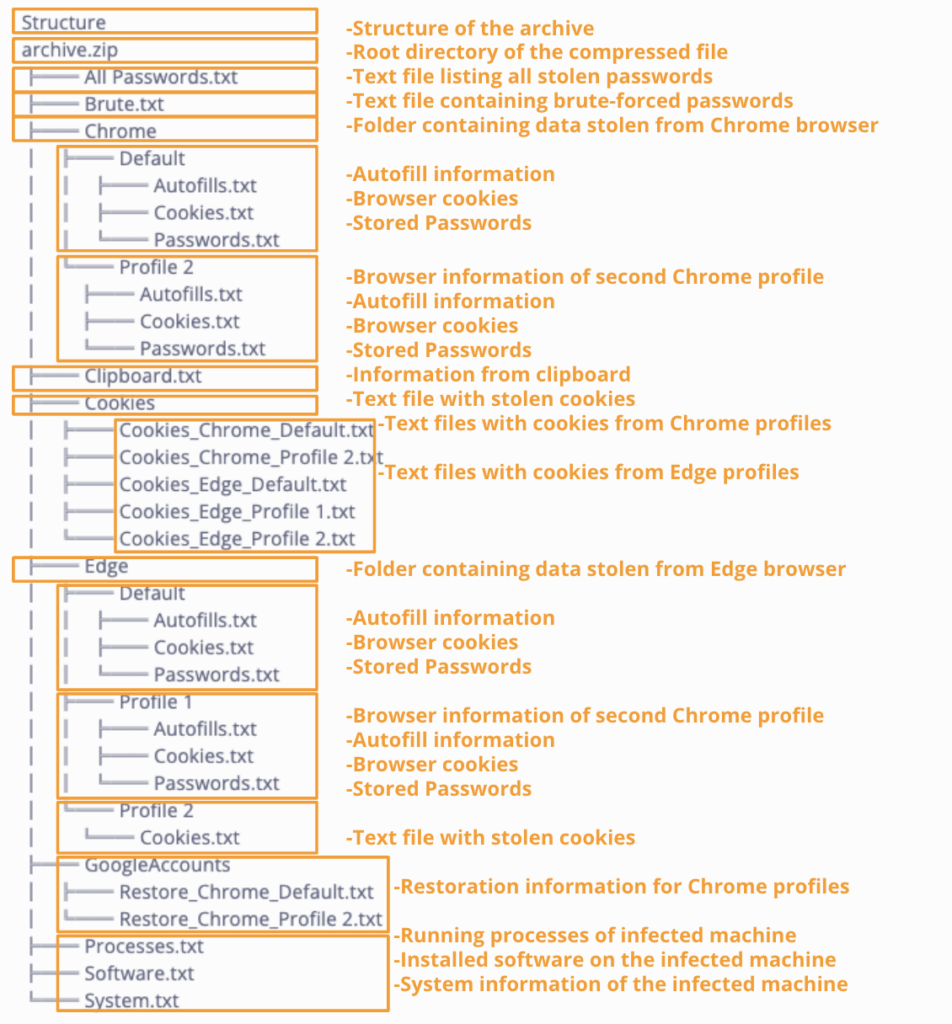
How do threat actors leverage logs in cyberattacks?
Stored passwords, browser cookies, autofill information, and other sensitive data are frequently captured in logs. Because of this, they are often the target of infostealer malware and other malicious activities. Unfortunately, as recent attacks have demonstrated, threat actors sometimes only need one weak password or compromised credential to infiltrate and disrupt systems. As such, the impact of compromised logs can be quite severe, leading to potential:
- Unauthorized access: Attackers can use stolen logs to gain entry to a victim’s systems, leading to data breaches, ransomware attacks, or further compromise of the network.
- Credential stuffing: Using automated tools, attackers can either test the information contained within logs across multiple sites or perform brute force attacks—exploiting users who reuse old passwords.
- Data exfiltration: Once inside, attackers can leverage infostealers to exfiltrate more sensitive data, leading to more elaborate attacks and larger campaigns.
Better protect your organization using Flashpoint
Logs are an indispensable tool for both security teams and threat actors. While logs are essential in detailing records that support security monitoring, compliance, and troubleshooting—they can unfortunately be used against organizations by attackers.
As cybersecurity threats such as infostealers and ransomware evolve, the importance of continuously monitoring the deep and dark web for illegal log listings is essential. Check out the following resources to learn more about developing cyber threats and what organizations can do to protect themselves:
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.

