Blog
Turning OSINT Into Action: How Monitor Helps Intel Analysts Tackle Data Overwhelm
Monitor—a new alerting and analysis capability from Flashpoint—helps intel analysts quickly and easily transform open-source data into actionable intelligence.

Data overload
Whether they are supporting corporate security operations centers or national security missions, intelligence teams everywhere face one common obstacle: data overload.
In recent years, security teams have realized the value of open-source intelligence (OSINT), which gives analysts an abundance of insights from public web sources. However, analysts today often struggle to process and make sense of the sheer volume of data on their desks. According to a 2020 Forrester study, almost 30% of security alerts are ignored due to time and resource constraints.
Without tools that can expedite open-source data collection and analysis, intelligence teams may overlook critical information and respond to risks. Thankfully, emerging technologies are helping analysts process and prioritize vast online datasets, many of which contain strategic security information from publicly available sources like social media, messaging apps, and the deep and dark web.
Introducing Monitor
Flashpoint’s powerful new capability, called Monitor, helps analysts turn raw online data into finished intelligence more efficiently. Monitor delivers a new set of capabilities that help intelligence analysts quickly and easily observe online chatter for threats and other pertinent security information over time. Monitor is included in Flashpoint Physical Security Intelligence (PSI; Formerly known as Echosec).
Related: Security Automation Crash Course: Which Workflows Should I Automate?
While Flashpoint PSI was initially built to support data discovery, Monitor allows users to discover, analyze, monitor, and disseminate the information gathered. Here’s how it works and what it might look like in your global security operations centre or national security team.
How Monitor works
Today, analysts use Flashpoint PSI to build specific keyword- and location-based searches across the platform’s social media and deep and dark web sources. Analysts then migrate searches over to the Monitor view (pictured below) where they can track new results and observe data analytics over time. In Monitor, analysts can also:
- View and share results with other analysts from the feature’s inbox
- Customize analytics widgets based on mission requirements
- Set alerts for time-sensitive events
- Locate results on a map (Flashpoint PSI uses machine learning to automatically tag results with inferred geographic locations)
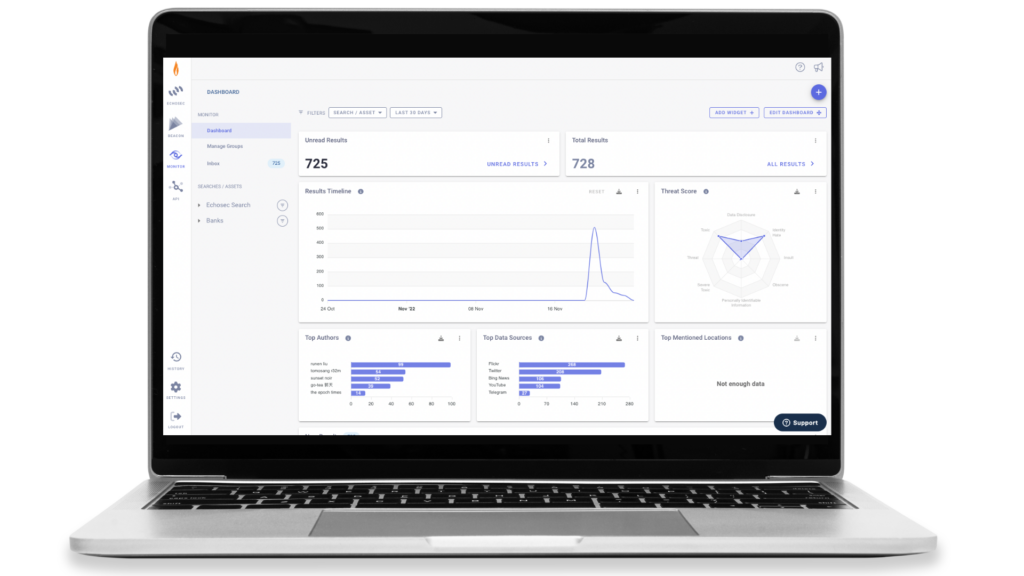
Monitor enables intelligence analysts to quickly understand if, when, and where critical events or patterns are happening. It’s also easy to use, minimizes analysis fatigue, and ensures that no information relevant to your security mission slips through the cracks.
Monitor use cases
Monitor is designed to support real-world security requirements for intelligence analysts in the public and private sectors. How does the feature support common security use cases?
Defense and geopolitical research
Defense intelligence analysts typically need to understand location-based activities such as military exercises and border activities. With Monitor, analysts can combine location- and keyword-based searches to detect new activities in a specific area in real time. Analysts can also observe analytics to anticipate future events, understand the type of threat involved, and narrow in on key actors.
Related: What Does a Cyber Threat Intel Analyst Do?
Event monitoring
Before a special event, analysts can use Flashpoint PSI to draw geofences over locations of interest, such as travel routes, embassies, or cities. Keyword searches can also be used to detect mentions of names or places relevant to an event. Viewing these searches in Monitor provides several insights: analysts can understand baseline activities in and around an event, detect immediate risks, and assess patterns in social activity volume and location.
Executive protection
Similarly to event monitoring, security professionals can assess an executive’s current or future whereabouts for potential risks over time by using Monitor to track locations and keywords of interest. An example of what this could look like would be to include an executive’s name as a keyword, and attach a threat or violence-related filter to the search to be alerted if the system detects any public posts that contain threatening language alongside the executive’s name.
In summary
As available security data expands and adversaries gain a strategic edge, intelligence leaders are more motivated than ever to give analysts tools that streamline the transformation of raw data into actionable intelligence. The goal of these solutions is twofold: make the analyst’s job easier and deliver intelligence that supports more accurate, timely security decisions.
If you’re an analyst working for an intelligence agency or a global security operations centre, you likely spend the majority of your time triaging, analyzing, and reporting on a barrage of alerts. What if your security software could offload some of these tasks, automatically monitoring data for relevant locations, trends, and insights over time? If your focus is open-source intelligence, Flashpoint PSI could be the solution you need.
To test Flashpoint PSI against your security use case, request a free trial.


